S. Zhang et al. / Future Generation Computer Systems 72 (2017) 227–238 229
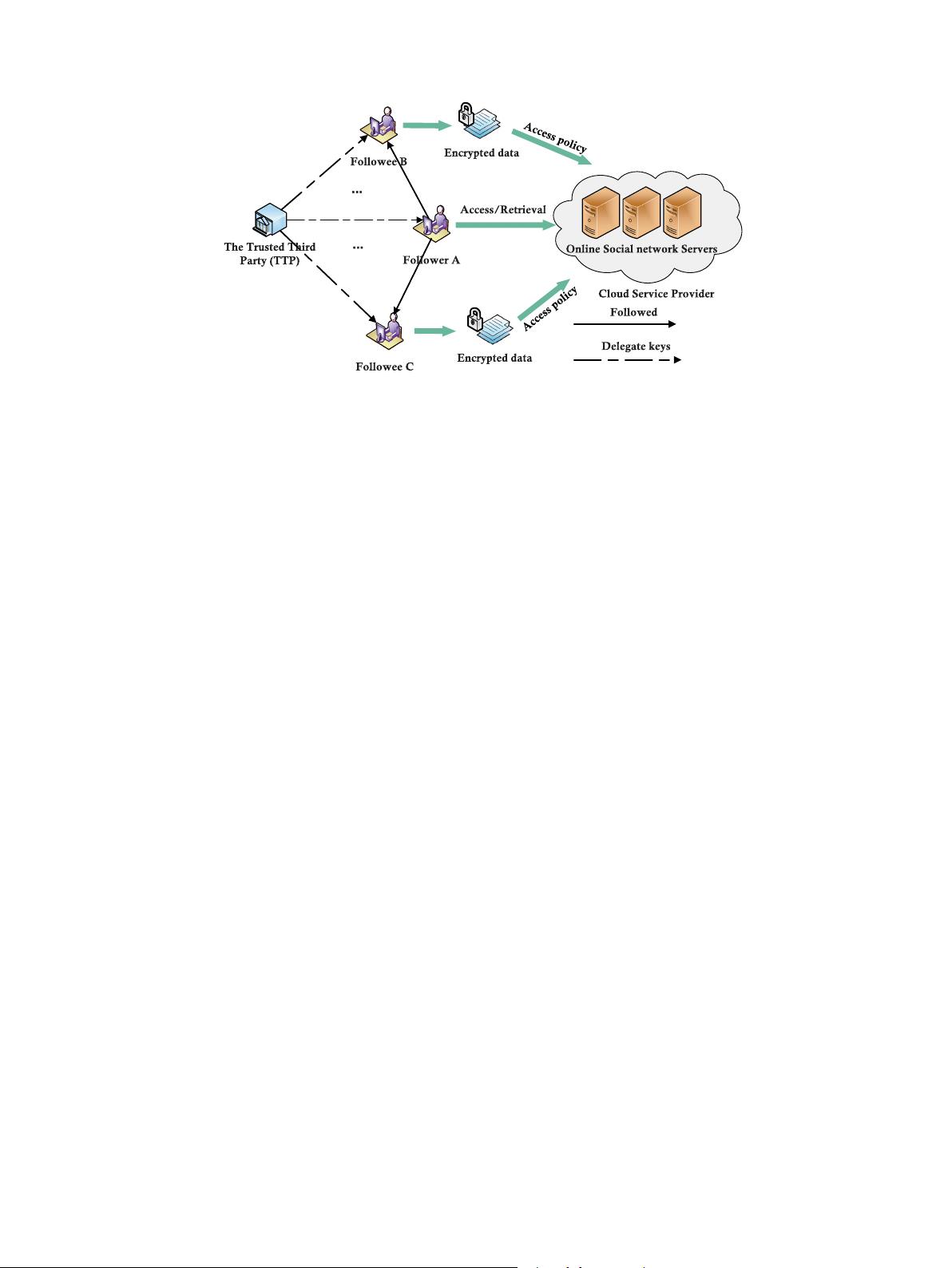
Fig. 1. The system model of the proposed scheme.
identity disclosure problem and resist the subgraph attack by
adding nodes and edges. Hay et al. [18] proposed a k-candidate
anonymity model through structural similarity. This algorithm
clusters vertices and edges into groups and anonymizes a
subgraph into a super-vertex. However, the graph may be shrank
considerably after anonymization. Obviously, these operations
influence the normal services of online social network.
Although these anonymization algorithms could preserve
privacy of individuals, they would decrease the utility of the
original social networks. Unlike aforementioned works, we try to
protect the privacy of authentic popularity of individual in online
social networks with full utility. The designed anonymization
method should take into account the privacy of user and the utility
of the online social networks.
3. Models and goals
3.1. System model
In our system model, four entities are involved, as illustrated
in Fig. 1. There are online social network servers, i.e., cloud
service provider (CSP), the trusted third party (TTP), followers,
and followees. The CSP operates a large number of interconnected
cloud servers with abundant storage capacity and computation
power to provide quality services. The main function of the TTP
is to generate secret keys and distribute keys for followers and
followees. The follower and followee are two different types of
online social network end-users. As seen from Fig. 1, if user A
follows user B, there is a directed edge from A and B, where A
is a follower and B is a followee. The in-degree of a followee
represents the user’s popularity. In order to provide social network
services, the followee first extracts several keywords from his
message file. Then, the followee encrypts the keywords and
corresponding message file using public key encryption, attribute-
based encryption method, respectively. Next, the followee sends
the encrypted keyword and corresponding message files to the
CSP. The follower can retrieve the encrypted files by a trapdoor.
Finally, the CSP returns the search results. If the attributes of the
follower satisfy the specific followee’s policy, he can decrypt this
followee’s encrypted message files. In a word, the system should
protect the users’ authentic popularity and provide core services
of OSNs, such as sharing/retrieving/reading the sensitive message
files, for followers and followees.
3.2. Threat model
Our goals include two aspects, on the one hand is to protect
the users’ authentic popularity while using the cloud-based social
network services, on the other hand is to achieve fine-grained
access control. In our threat model, we assume that the TTP and
followees are trusted. However, the CSP is considered as ‘‘honest
but curious’’ entity. That is to say, the CSP will honestly run the
protocol, but it is ‘‘curious’’ to infer and analyze the user’s interest
keyword, user’s message files and user’s authentic popularity so
as to learn some additional information about the stored data.
The unauthorized followers may also try to acquire the authentic
popularity of followee to make commercial advertisements and
tend to access the message files outside their permissions. We also
assume the transmission channels between all parts are protected
with standard security protocols such as SSL and SSH. In reality, as
the follower and the CSP belongs to different parties, they have no
common interests. Thus, we assume that they will not collude to
compromise the followee’s privacy.
We will consider keyword privacy, message file privacy, query
privacy and users’ authentic popularity privacy. Keyword privacy
is considered to be compromised if the following cases happen: (1)
The CSP knows the contents of some keywords on its platform.
(2) The CSP knows some message files containing some specific
keyword. Message file privacy is considered to be compromised
if the following cases happen: (1) The CSP knows the contents of
message files stored on its platform; (2) An untrusted follower
can access the unauthorized message files. Query privacy is
considered to be compromised if the following cases happen: (1)
The CSP knows the query keywords issued by the followers. (2)
A unauthorized follower can generate valid queries to search the
relevance message files without obtaining authorization from the
followee. The privacy of user’s authentic popularity is considered
to be compromised if the following case happens: The CSP or a
follower can obtain the authentic popularity of the followee.
3.3. Design goals
To protect the privacy of the authentic popularity of followee
while keeping the full utility of online social networks, our system
design should achieve the following security and performance
guarantees.
• Effective authentic popularity hiding mechanism: To design an
anonymization scheme which can not only hide the followees’
authentic popularity from CSP and followers but also keep the
full utility of online social network.









