"CSK和DCSK与MC-DCSK的原理与实现代码"
需积分: 49 201 浏览量
更新于2024-01-20
4
收藏 1.8MB DOCX 举报
混沌移位键控CSK(Chaotic Shift Keying)和DCSK(Differential Chaotic Shift Keying)是一种基于混沌映射的调制解调技术,与MC-DCSK(Multi-Carrier Differential Chaotic Shift Keying)相比,具有更高的抗噪声性能和更低的误码率。
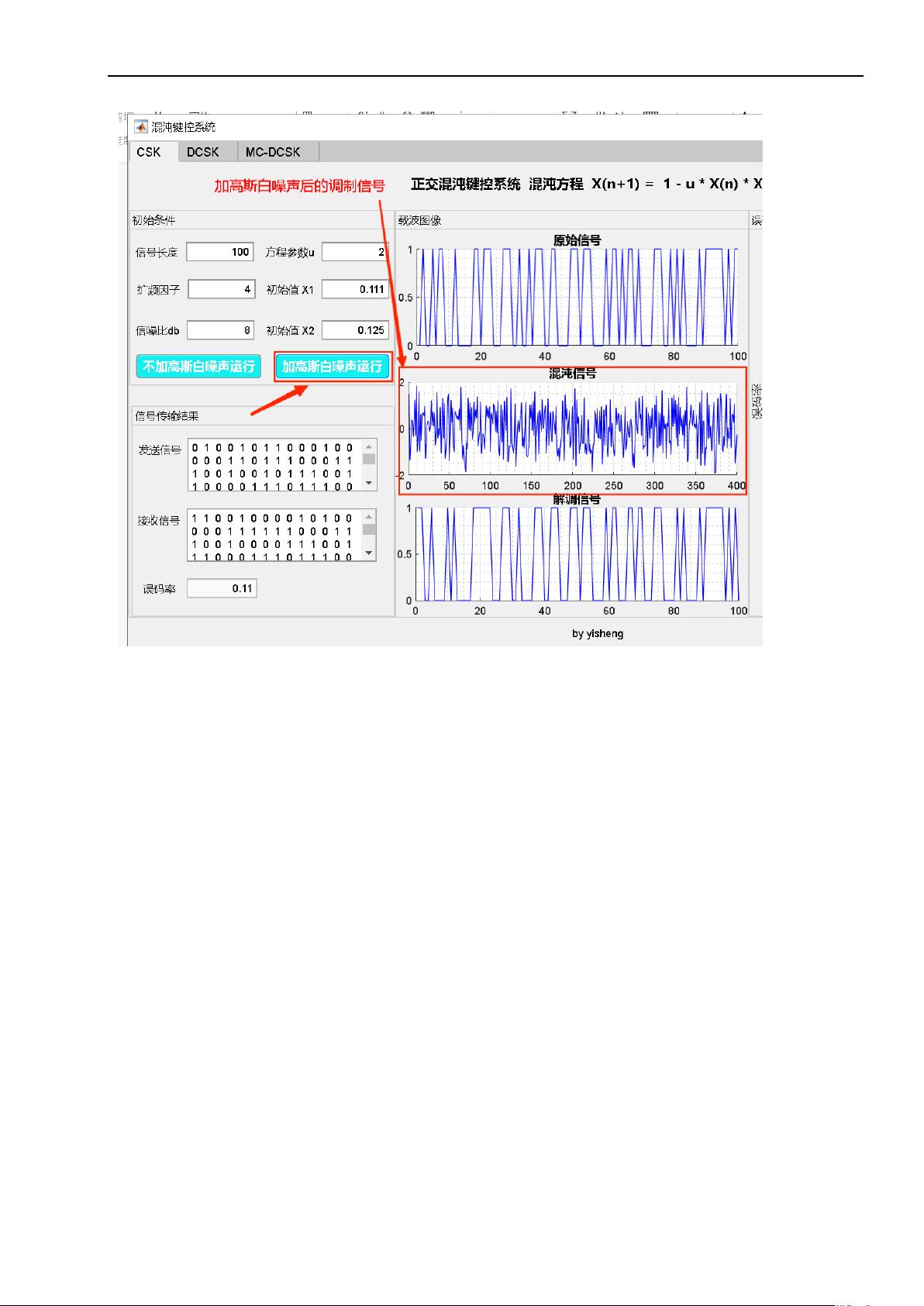
CSK是一种非相干调制方式,其调制原理是将二进制信息序列映射到混沌信号的极性反转时刻,即在每个信号周期的极性变换时刻改变混沌信号的系数。通过使用不同的阈值来解调信号,并将其映射回二进制序列,实现数据的传输。
DCSK是一种差分调制方式,其调制原理是通过混沌信号的极性差异来表示二进制信息。在调制过程中,通过比较相邻两个信号周期的极性差异,将其映射为二进制序列。
MC-DCSK是一种多载波混沌调制方式,通过将混沌信号应用于多个载波频率上,来实现更好的抗噪声性能。在解调过程中,通过计算多个载波频率上的混沌信号与已调信号之间的差异,将其映射回二进制序列。
在实际实验中,首先完成了CSK的调制和解调功能。通过输入二进制序列,可以观察到调制后的波形,并通过相干解调输出二进制序列。随后,引入高斯白噪声的干扰,进行了相同的解调过程,并计算出误码率。实验结果表明,在不同信噪比环境下,CSK具有良好的抗噪声性能和较低的误码率。
实验中采用了Matlab和Matlab App designer作为实验工具,并根据实验要求进行了相应的步骤和结果记录。在实验原理部分,介绍了CSK调制解调的基本原理,并说明了混沌映射的原理和应用。在实验步骤及结果部分,详细描述了实验过程和实验结果,并给出了在不同信噪比环境下的误码率分析图。
总结而言,混沌移位键控CSK和DCSK与MC-DCSK是基于混沌映射的调制解调技术,在实验中展示了它们的原理和实现代码。通过实验结果可以看出,这些技术具有较好的抗噪声性能和较低的误码率,适用于数据通信安全技术领域。
2024-07-18 上传
136 浏览量
136 浏览量
点击了解资源详情
2021-02-25 上传
点击了解资源详情
点击了解资源详情
qinyanshen
- 粉丝: 5
最新资源
- 网页自动刷新工具 v1.1 - 自定义时间间隔与关机
- pt-1.4协程源码深度解析
- EP4CE6E22C8芯片三相正弦波发生器设计与实现
- 高效处理超大XML文件的查看工具介绍
- 64K极限挑战:国际程序设计大赛优秀3D作品展
- ENVI软件全面应用教程指南
- 学生档案管理系统设计与开发
- 网络伪书:社区驱动的在线音乐制图平台
- Lettuce 5.0.3中文API文档完整包下载指南
- 雅虎通Yahoo! Messenger v0.8.115即时聊天功能详解
- 将Android手机转变为IP监控摄像机
- PLSQL入门教程:变量声明与程序交互
- 掌握.NET三层架构:实例学习与源码解析
- WPF中Devexpress GridControl分组功能实例分析
- H3Viewer: VS2010专用高效帮助文档查看工具
- STM32CubeMX LED与按键初始化及外部中断处理教程