Secure Namespaced Kernel Audit for Containers SoCC ’21, November 1–4, 2021, Seale, WA, USA
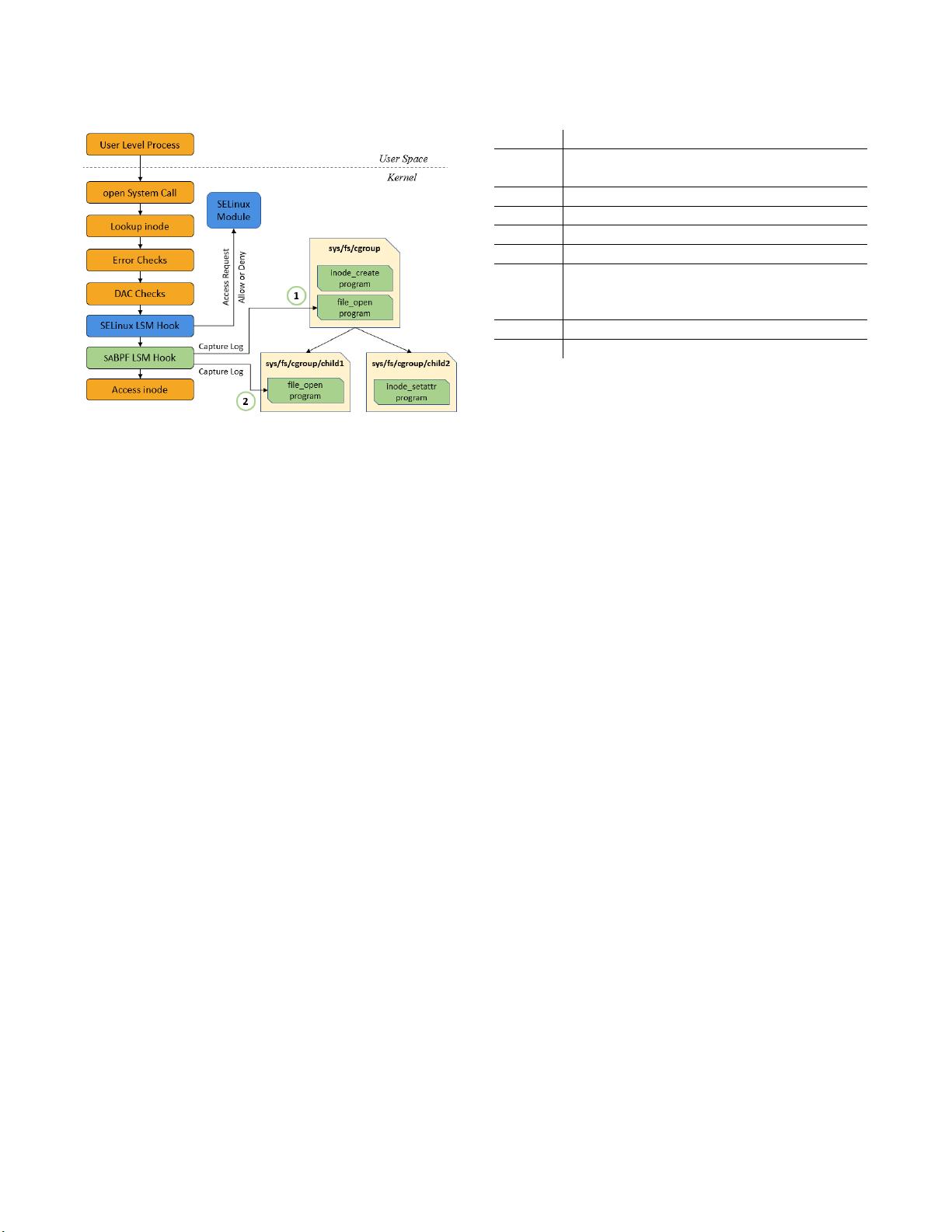
Figure 2: LSM hook architecture [
46
]. The green blocks
are sp ecic to saBPF, which is describ ed in § 3.
1
○
shows
programs attached to the root cgroup;
2
○
shows two
programs attached to the
child1
and
child2
cgroup
respectively.
of mandatory access control scheme [
56
]. As a reference mon-
itor, LSM has also been adapted to perform secure kernel log-
ging, which provides stronger completeness and faithfulness
guarantees than traditional audit systems [
17
,
51
,
54
]. For
example, prior research has veried that LSM hooks capture
all meaningful interactions between kernel objects [
22
,
36
]
and that information ow within the kernel can be observed
by at least one LSM hook [
27
], which is necessary to achieve
completeness.
The LSM framework does not use system call interposi-
tion as older systems did. Syscall interposition is susceptible
to concurrency vulnerabilities, which in turn lead to time-
of-check-to-time-of-use (TOCTTOU) attacks that result in
discrepancies between the events as seen by the security
mechanism and the system call logic [
66
,
67
]. This is why
solutions such as kprobe-BPF, while useful for performance
analysis, are not appropriate to build security tools. Instead,
LSM’s reference-monitor design ensures that the relevant
kernel states and objects are immutable when a hook is
triggered, which is necessary to achieve faithfulness. LSM-
BPF [
57
] is a recent extension to the eBPF framework that
provides a more secure mechanism to implement security
functionalities on LSM hooks.
2.3 Namespaces in Linux
A namespace in the Linux kernel is an abstract environment
in which processes within the namespace appear to own an
independent instance of system resources. Changes to those
Name Description
cgroup
Allocate system resource (e.g., CPU, memory,
and networking)
ipc Isolate inter-process communications
network Virtualize the network stack
mount Control mount points
process Provide independent process IDs
user
Provide independent user IDs and group IDs,
and give privileges (or capabilities) associated
with those IDs within other namespaces
UTS Change host and domain names
Time See dierent system times
Table 1: Summary of Linux namespaces.
resources are not visible to processes outside the namespace.
We summarize available namespaces in Linux in Table 1.
One prominent use of namespaces is to create contain-
ers. For example, an application in a Docker container runs
within its own set of namespaces. Kubernetes “pods” contain
one or more containers so that they share namespaces (and
therefore system resources). Kubernetes makes it appear to
applications within a pod that they own a machine of their
own (Fig. 3).
saBPF modies the kernel to enable per-container audit-
ing, selectively invoking eBPF programs on LSM hooks based
on
cgroup
membership (§ 3.1).
cgroup
isolates processes’
resource usage in a hierarchical fashion, with a child group
having additional restrictions to those of its parent. Since
cgroup
v2 [
35
], this hierarchy is system-wide, and all pro-
cesses initially belong to the root
cgroup
. In a Kubernetes
pod, for example, containers can be organized in a hierarchi-
cal structure and assigned various
cgroup
namespaces to set
up further restrictions. Certain types of eBPF programs, such
as the ones that are socket-related, can already be attached
to
cgroup
s (e.g.,
BPF_PROG_TYPE_CGROUP_SKB
). This allows,
for example, a packet ltering program to apply network
lters to sockets of all processes within a particular con-
tainer. saBPF makes it possible to attach eBPF programs at
the intersection of
cgroup
s and LSM hooks (§ 3.1) for audit
purpose and beyond (§ 4).
3 SABPF: EXTENDING THE EBPF
FRAMEWORK
saBPF extends the eBPF framework to support secure ker-
nel auditing in a containerized environment. Our design
is minimally invasive, reusing existing components in the
framework as much as possible and extending only what
we deemed to be necessary. This is a conscious decision
made to achieve two objectives: 1) by adhering closely to the









