nonself discrimination, and meanwhile provides grounding
for the immune response. In one such danger theory model,
APC receives the signal of harmful bacteria to create signal
zero; such signal activates antigenic-presenting cells to
create signal two which helps T cells react to harmful
materials, and hence the immune response is triggered.
Though this theory has not been completely accepted in the
immunology community, it becomes popular amongst
immunologists. It gives us a fundamental indication of how
an immune response is initialized, and also leads to a
number of potential inspirations for AIS. Especially, it
might be a useful source of inspiration in studying DCO. In
this research, some valuable characteristics from the danger
theory are adopted:
A. Dynamic surveillance. The immune system detects or
identifies online whether external pathogens arrive. If
some cells are infected, such system is trigged,
meanwhile the danger is found.
B. Distinctive response. The intruding danger damages
immune cells and living organisms. Different dangers
results in different responses.
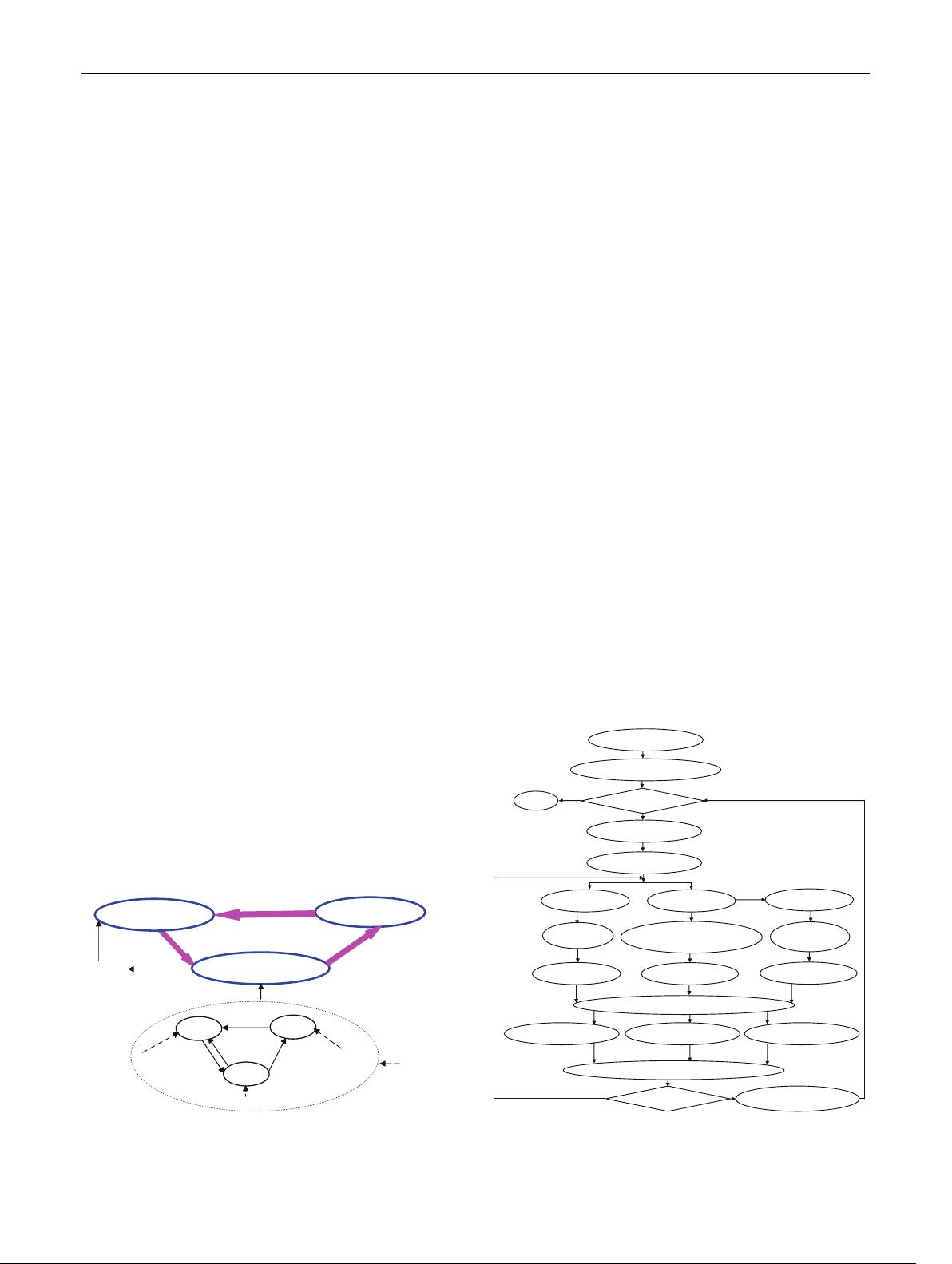
Figure 1 below displays an artificial immune model
based on the danger theory, where the symbols of B-cell,
T-cell and M-cell represent B, T and memory cells,
respectively. This model is composed of danger detection,
immune evolution and memory pool. The first module is to
discover the danger as well as to decide the level of the
danger, and transmit the level to the second module. After
receiving the level, the second module carries out indi-
vidual evolution, and ultimately creates plasma cells
capable of eliminating the danger. In the process of evo-
lution, the initial B cells are first created in terms of the
level. Subsequently, B, T and memory cells co-evolve in
the same environment so that the danger is deleted. The last
module collects the eventual memory cells; when some
previous danger does not appear again, only the corre-
spondingly best memory cell found is admitted to store into
the memory pool, due to computational complexity.
5 Algorithm statement and design
5.1 Algorithm formulation
For a given environment t, danger Ag(t) stands for an
attribute set, AgðtÞfXðtÞ; pðtÞ; IðtÞ; JðtÞ; f ð:; tÞ; Gð:; tÞg;
where G(., t) represents the vector-valued function descri-
bed by the constraints in Sect. 3; B cells and T cells are all
regarded as real-valued candidates, and memory cells
denote those better B cells found until the current evolving
population in the environment. Here, an integer variant
C
hange
is introduced to represent whether the current
environment changes. It takes 0 if the environment keeps
no change and 1 otherwise. Another integer variant L
evel
means the level of the danger, only taking 1, 2 and 3. It is
prescribed that in comparison to the previous environ-
ments, if the current environment makes a drastic change
(i.e., such environment differs from the previous ones
completely), L
evel
takes 1, but 2 or 3 for a medium or small
change; more explanations can be known below. This way,
by means of Fig. 1 we can draw the flowchart in Fig. 2
above. It consists of an outer loop and an inner one; the first
updates the memory pool, while justifying whether the
procedure ends; the second executes an loop of optimiza-
tion, also detects online whether the current environment
takes a change and decides the level of the coming danger.
Correspondingly, the algorithm formulation is given as
follows:
Danger
Output
Danger detection
Elimination
Input
Transmit signal
Memory cell
Immune evolution
Memory pool
Assistance
T-cell
Learning
M-cell
Reaction
Genetic drift
B-cell
Co-evolution
Fig. 1 Artificial immune optimization model
t =0, Change=0, Level=0
Parameter settings
Change=0 ?
Initial population
Population division
Population B
c
Population T
c
Proliferation, mutation
Selection
Population M
c
Danger detection
Population T
*
c
Population B
*
c
New population T
c
New population B
c
New population M
c
t ++
Communication between populations
Population M
*
c
Update memory pool M
p
t <T?
Copy
End
Yes
Yes
No
No
Reaction
Selection
Genetic drift
Selection
Fig. 2 Flowchart of DTAIS
Danger theory based artificial immune system 189
123









