没有合适的资源?快使用搜索试试~ 我知道了~
首页计算机网络系统方法:第五版精华概览
计算机网络系统方法:第五版精华概览
"计算机网络系统方法,第五版(英文版)" 是一本深入探讨计算机网络的专著,书中从系统的方法论出发,详细阐述了网络的基础、直接连接、互连网络、高级互连、端到端协议以及拥塞控制与资源分配等多个核心主题。
在第一章“基础”中,作者首先介绍了各种应用程序,这些应用对网络提出了多样化的需求,包括但不限于数据传输、文件共享、视频流等。接着,详细讨论了网络必须满足的要求,如可靠传输、高效能、安全性等。网络架构是这一章的重点,它涵盖了网络的分层模型和不同层次的功能。此外,软件部分讨论了网络协议栈的实现和操作系统在网络中的作用。性能分析部分则涵盖了带宽、延迟、吞吐量和丢包率等关键性能指标。
第二章“直接连接”聚焦于两个设备之间的物理和逻辑连接。视角从连接设备的视角出发,探讨了编码技术,如何在物理媒介上传输比特流,以及帧定界的重要性。错误检测通过校验和和循环冗余校验(CRC)等方法确保数据的完整性。可靠的传输机制,如停等协议和滑动窗口协议,用于在有错误的链路上恢复数据。多址访问网络(如局域网)和无线网络的特性也被详细解析。
第三章“互连网络”主要关注交换和桥接技术,以及基本的互连方案,如路由器的工作原理。路由选择算法和协议是本章的另一重点,包括距离矢量和链路状态路由协议。此外,还探讨了互连网络的具体实施细节。
第四章“高级互连”进一步深入,讲解全球互联网的运行机制,包括IP地址分配和DNS系统。多播技术允许高效地向多个接收者发送数据。多协议标签交换(MPLS)提供了更高效的路径选择。移动设备间的路由问题也得到了关注,以适应移动计算环境。
第五章“端到端协议”中,简单多路复用器(UDP)和可靠字节流(TCP)这两种主要的传输层协议被详细解析。远程过程调用(RPC)用于跨网络的程序间通信,而实时应用如RTP提供了对低延迟和抖动敏感的数据传输支持。
第六章“拥塞控制和资源分配”探讨了网络中资源的管理和分配问题,包括拥塞的发生、检测和避免策略,以及公平性和效率的平衡。本章还涉及QoS(服务质量)机制,如优先级队列和流量整形。
这本《计算机网络系统方法》全面覆盖了网络设计、实现和管理的关键概念,对于理解网络原理和技术的深度和广度都极具价值。无论是初学者还是经验丰富的专业人士,都能从中受益匪浅。

Thereareseveraldifferentmethodsformultiplexingmultipleflowsontoonephysicallink.Onecommonmethodis
synchronoustime-divisionmultiplexing(STDM).TheideaofSTDMistodividetimeintoequal-sizedquantaand,ina
round-robinfashion,giveeachflowachancetosenditsdataoverthephysicallink.Inotherwords,duringtime
quantum1,datafromS1toR1istransmitted;duringtimequantum2,datafromS2toR2istransmitted;inquantum3,
S3sendsdatatoR3.Atthispoint,thefirstflow(S1toR1)getstogoagain,andtheprocessrepeats.Anothermethod
isfrequency-divisionmultiplexing(FDM).TheideaofFDMistotransmiteachflowoverthephysicallinkatadifferent
frequency,muchthesamewaythatthesignalsfordifferentTVstationsaretransmittedatadifferentfrequencyover
theairwavesoronacoaxialcableTVlink.
Althoughsimpletounderstand,bothSTDMandFDMarelimitedintwoways.First,ifoneoftheflows(hostpairs)
doesnothaveanydatatosend,itsshareofthephysicallink—thatis,itstimequantumoritsfrequency—remainsidle,
evenifoneoftheotherflowshasdatatotransmit.Forexample,S3hadtowaititsturnbehindS1andS2inthe
previousparagraph,evenifS1andS2hadnothingtosend.Forcomputercommunication,theamountoftimethata
linkisidlecanbeverylarge—forexample,considertheamountoftimeyouspendreadingawebpage(leavingthe
linkidle)comparedtothetimeyouspendfetchingthepage.Second,bothSTDMandFDMarelimitedtosituationsin
whichthemaximumnumberofflowsisfixedandknownaheadoftime.Itisnotpracticaltoresizethequantumorto
addadditionalquantainthecaseofSTDMortoaddnewfrequenciesinthecaseofFDM.
Theformofmultiplexingthataddressestheseshortcomings,andofwhichwemakemostuseinthisbook,iscalled
statisticalmultiplexing.Althoughthenameisnotallthathelpfulforunderstandingtheconcept,statisticalmultiplexing
isreallyquitesimple,withtwokeyideas.First,itislikeSTDMinthatthephysicallinkissharedovertime—firstdata
fromoneflowistransmittedoverthephysicallink,thendatafromanotherflowistransmitted,andsoon.Unlike
STDM,however,dataistransmittedfromeachflowondemandratherthanduringapredeterminedtimeslot.Thus,if
onlyoneflowhasdatatosend,itgetstotransmitthatdatawithoutwaitingforitsquantumtocomearoundandthus
withouthavingtowatchthequantaassignedtotheotherflowsgobyunused.Itisthisavoidanceofidletimethat
givespacketswitchingitsefficiency.
Asdefinedsofar,however,statisticalmultiplexinghasnomechanismtoensurethatalltheflowseventuallygettheir
turntotransmitoverthephysicallink.Thatis,onceaflowbeginssendingdata,weneedsomewaytolimitthe
transmission,sothattheotherflowscanhaveaturn.Toaccountforthisneed,statisticalmultiplexingdefinesan
upperboundonthesizeoftheblockofdatathateachflowispermittedtotransmitatagiventime.Thislimited-size
blockofdataistypicallyreferredtoasapacket,todistinguishitfromthearbitrarilylargemessagethatanapplication
programmightwanttotransmit.Becauseapacket-switchednetworklimitsthemaximumsizeofpackets,ahostmay
notbeabletosendacompletemessageinonepacket.Thesourcemayneedtofragmentthemessageintoseveral
packets,withthereceiverreassemblingthepacketsbackintotheoriginalmessage.
Inotherwords,eachflowsendsasequenceofpacketsoverthephysicallink,withadecisionmadeonapacket-by-
packetbasisastowhichflow'spackettosendnext.Noticethat,ifonlyoneflowhasdatatosend,thenitcansenda
sequenceofpacketsback-to-back;however,shouldmorethanoneoftheflowshavedatatosend,thentheirpackets
areinterleavedonthelink.depictsaswitchmultiplexingpacketsfrommultiplesourcesontoasinglesharedlink.
Thedecisionastowhichpackettosendnextonasharedlinkcanbemadeinanumberofdifferentways.For
example,inanetworkconsistingofswitchesinterconnectedbylinkssuchastheoneinFigure4,thedecisionwould
bemadebytheswitchthattransmitspacketsontothesharedlink.(Aswewillseelater,notallpacket-switched
networksactuallyinvolveswitches,andtheymayuseothermechanismstodeterminewhosepacketgoesontothe
linknext.)Eachswitchinapacket-switchednetworkmakesthisdecisionindependently,onapacket-by-packetbasis.
Oneoftheissuesthatfacesanetworkdesignerishowtomakethisdecisioninafairmanner.Forexample,aswitch
couldbedesignedtoservicepacketsonafirst-in,first-out(FIFO)basis.Anotherapproachwouldbetotransmitthe
packetsfromeachofthedifferentflowsthatarecurrentlysendingdatathroughtheswitchinaround-robinmanner.
Thismightbedonetoensurethatcertainflowsreceiveaparticularshareofthelink'sbandwidthorthattheynever
havetheirpacketsdelayedintheswitchformorethanacertainlengthoftime.Anetworkthatattemptstoallocate
bandwidthtoparticularflowsissometimessaidtosupportqualityofservice(QoS),atopicthatwereturntoinChapter
6.
1.2Requirements
16
Also,noticeinFigure4thatsincetheswitchhastomultiplexthreeincomingpacketstreamsontooneoutgoinglink,it
ispossiblethattheswitchwillreceivepacketsfasterthanthesharedlinkcanaccommodate.Inthiscase,theswitchis
forcedtobufferthesepacketsinitsmemory.Shouldaswitchreceivepacketsfasterthanitcansendthemforan
extendedperiodoftime,thentheswitchwilleventuallyrunoutofbufferspace,andsomepacketswillhavetobe
dropped.Whenaswitchisoperatinginthisstate,itissaidtobecongested.
Thebottomlineisthatstatisticalmultiplexingdefinesacost-effectivewayformultipleusers(e.g.,host-to-hostflowsof
data)tosharenetworkresources(linksandnodes)inafine-grainedmanner.Itdefinesthepacketasthegranularity
withwhichthelinksofthenetworkareallocatedtodifferentflows,witheachswitchabletoscheduletheuseofthe
physicallinksitisconnectedtoonaper-packetbasis.Fairlyallocatinglinkcapacitytodifferentflowsanddealingwith
congestionwhenitoccursarethekeychallengesofstatisticalmultiplexing.
SupportforCommonServices
Theprevioussectionoutlinedthechallengesinvolvedinprovidingcost-effectiveconnectivityamongagroupofhosts,
butitisoverlysimplistictoviewacomputernetworkassimplydeliveringpacketsamongacollectionofcomputers.It
ismoreaccuratetothinkofanetworkasprovidingthemeansforasetofapplicationprocessesthataredistributed
overthosecomputerstocommunicate.Inotherwords,thenextrequirementofacomputernetworkisthatthe
applicationprogramsrunningonthehostsconnectedtothenetworkmustbeabletocommunicateinameaningful
way.Fromtheapplicationdeveloper'sperspective,thenetworkneedstomakehisorherlifeeasier.
Whentwoapplicationprogramsneedtocommunicatewitheachother,alotofcomplicatedthingsmusthappen
beyondsimplysendingamessagefromonehosttoanother.Oneoptionwouldbeforapplicationdesignerstobuildall
thatcomplicatedfunctionalityintoeachapplicationprogram.However,sincemanyapplicationsneedcommon
services,itismuchmorelogicaltoimplementthosecommonservicesonceandthentolettheapplicationdesigner
buildtheapplicationusingthoseservices.Thechallengeforanetworkdesigneristoidentifytherightsetofcommon
services.Thegoalistohidethecomplexityofthenetworkfromtheapplicationwithoutoverlyconstrainingthe
applicationdesigner.
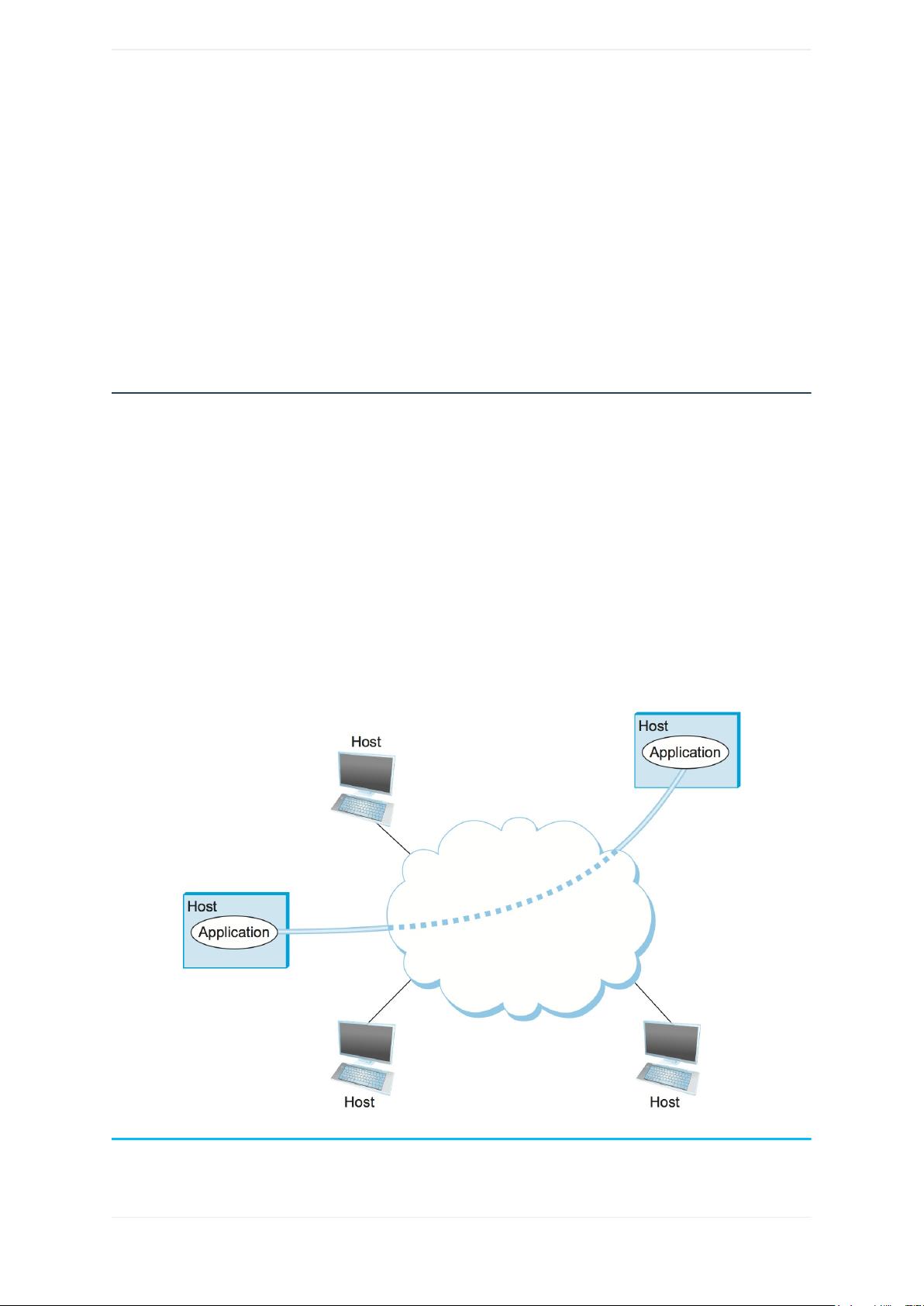
Figure5.Processescommunicatingoveranabstractchannel.
1.2Requirements
17
Intuitively,weviewthenetworkasprovidinglogicalchannelsoverwhichapplication-levelprocessescancommunicate
witheachother;eachchannelprovidesthesetofservicesrequiredbythatapplication.Inotherwords,justasweuse
acloudtoabstractlyrepresentconnectivityamongasetofcomputers,wenowthinkofachannelasconnectingone
processtoanother.Figure5showsapairofapplication-levelprocessescommunicatingoveralogicalchannelthatis,
inturn,implementedontopofacloudthatconnectsasetofhosts.Wecanthinkofthechannelasbeinglikeapipe
connectingtwoapplications,sothatasendingapplicationcanputdatainoneendandexpectthatdatatobe
deliveredbythenetworktotheapplicationattheotherendofthepipe.
Thechallengeistorecognizewhatfunctionalitythechannelsshouldprovidetoapplicationprograms.Forexample,
doestheapplicationrequireaguaranteethatmessagessentoverthechannelaredelivered,orisitacceptableif
somemessagesfailtoarrive?Isitnecessarythatmessagesarriveattherecipientprocessinthesameorderinwhich
theyaresent,ordoestherecipientnotcareabouttheorderinwhichmessagesarrive?Doesthenetworkneedto
ensurethatnothirdpartiesareabletoeavesdroponthechannel,orisprivacynotaconcern?Ingeneral,anetwork
providesavarietyofdifferenttypesofchannels,witheachapplicationselectingthetypethatbestmeetsitsneeds.
Therestofthissectionillustratesthethinkinginvolvedindefiningusefulchannels.
IdentifyingCommonCommunicationPatterns
Designingabstractchannelsinvolvesfirstunderstandingthecommunicationneedsofarepresentativecollectionof
applications,thenextractingtheircommoncommunicationrequirements,andfinallyincorporatingthefunctionalitythat
meetstheserequirementsinthenetwork.
OneoftheearliestapplicationssupportedonanynetworkisafileaccessprogramliketheFileTransferProtocol
(FTP)orNetworkFileSystem(NFS).Althoughmanydetailsvary—forexample,whetherwholefilesaretransferred
acrossthenetworkoronlysingleblocksofthefileareread/writtenatagiventime—thecommunicationcomponentof
remotefileaccessischaracterizedbyapairofprocesses,onethatrequeststhatafilebereadorwrittenanda
secondprocessthathonorsthisrequest.Theprocessthatrequestsaccesstothefileiscalledtheclient,andthe
processthatsupportsaccesstothefileiscalledtheserver.
Readingafileinvolvestheclientsendingasmallrequestmessagetoaserverandtheserverrespondingwithalarge
messagethatcontainsthedatainthefile.Writingworksintheoppositeway—theclientsendsalargemessage
containingthedatatobewrittentotheserver,andtheserverrespondswithasmallmessageconfirmingthatthewrite
todiskhastakenplace.
Adigitallibraryisamoresophisticatedapplicationthanfiletransfer,butitrequiressimilarcommunicationservices.
Forexample,theAssociationforComputingMachinery(ACM)operatesalargedigitallibraryofcomputerscience
literatureat
http://portal.acm.org/dl.cfm
Thislibraryhasawiderangeofsearchingandbrowsingfeaturestohelpusersfindthearticlestheywant,but
ultimatelymuchofwhatitdoesisrespondtouserrequestsforfiles,suchaselectroniccopiesofjournalarticles,much
likeanFTPserver.
Usingfileaccess,adigitallibrary,andthetwovideoapplicationsdescribedintheintroduction(videoconferencingand
videoondemand)asarepresentativesample,wemightdecidetoprovidethefollowingtwotypesofchannels:
request/replychannelsandmessagestreamchannels.Therequest/replychannelwouldbeusedbythefiletransfer
anddigitallibraryapplications.Itwouldguaranteethateverymessagesentbyonesideisreceivedbytheotherside
andthatonlyonecopyofeachmessageisdelivered.Therequest/replychannelmightalsoprotecttheprivacyand
integrityofthedatathatflowsoverit,sothatunauthorizedpartiescannotreadormodifythedatabeingexchanged
betweentheclientandserverprocesses.
1.2Requirements
18

Themessagestreamchannelcouldbeusedbyboththevideoondemandandvideoconferencingapplications,
provideditisparameterizedtosupportbothone-wayandtwo-waytrafficandtosupportdifferentdelayproperties.The
messagestreamchannelmightnotneedtoguaranteethatallmessagesaredelivered,sinceavideoapplicationcan
operateadequatelyevenifsomevideoframesarenotreceived.Itwould,however,needtoensurethatthose
messagesthataredeliveredarriveinthesameorderinwhichtheyweresent,toavoiddisplayingframesoutof
sequence.Liketherequest/replychannel,themessagestreamchannelmightwanttoensuretheprivacyandintegrity
ofthevideodata.Finally,themessagestreamchannelmightneedtosupportmulticast,sothatmultiplepartiescan
participateintheteleconferenceorviewthevideo.
Whileitiscommonforanetworkdesignertostriveforthesmallestnumberofabstractchanneltypesthatcanserve
thelargestnumberofapplications,thereisadangerintryingtogetawaywithtoofewchannelabstractions.Simply
stated,ifyouhaveahammer,theneverythinglookslikeanail.Forexample,ifallyouhavearemessagestreamand
request/replychannels,thenitistemptingtousethemforthenextapplicationthatcomesalong,evenifneithertype
providesexactlythesemanticsneededbytheapplication.Thus,networkdesignerswillprobablybeinventingnew
typesofchannels—andaddingoptionstoexistingchannels—foraslongasapplicationprogrammersareinventing
newapplications.
Alsonotethatindependentofexactlywhatfunctionalityagivenchannelprovides,thereisthequestionofwherethat
functionalityisimplemented.Inmanycases,itiseasiesttoviewthehost-to-hostconnectivityoftheunderlying
networkassimplyprovidingabitpipe,withanyhigh-levelcommunicationsemanticsprovidedattheendhosts.The
advantageofthisapproachisthatitkeepstheswitchesinthemiddleofthenetworkassimpleaspossible—they
simplyforwardpackets—butitrequirestheendhoststotakeonmuchoftheburdenofsupportingsemanticallyrich
process-to-processchannels.Thealternativeistopushadditionalfunctionalityontotheswitches,therebyallowingthe
endhoststobe"dumb"devices(e.g.,telephonehandsets).Wewillseethisquestionofhowvariousnetworkservices
arepartitionedbetweenthepacketswitchesandtheendhosts(devices)asarecurringissueinnetworkdesign.
Reliability
Assuggestedbytheexamplesjustconsidered,reliablemessagedeliveryisoneofthemostimportantfunctionsthata
networkcanprovide.Itisdifficulttodeterminehowtoprovidethisreliability,however,withoutfirstunderstandinghow
networkscanfail.Thefirstthingtorecognizeisthatcomputernetworksdonotexistinaperfectworld.Machines
crashandlaterarerebooted,fibersarecut,electricalinterferencecorruptsbitsinthedatabeingtransmitted,switches
runoutofbufferspace,and,asifthesesortsofphysicalproblemsaren'tenoughtoworryabout,thesoftwarethat
managesthehardwaremaycontainbugsandsometimesforwardspacketsintooblivion.Thus,amajorrequirementof
anetworkistorecoverfromcertainkindsoffailures,sothatapplicationprogramsdon'thavetodealwiththemoreven
beawareofthem.
Therearethreegeneralclassesoffailurethatnetworkdesignershavetoworryabout.First,asapacketistransmitted
overaphysicallink,biterrorsmaybeintroducedintothedata;thatis,a1isturnedintoa0orviceversa.Sometimes
singlebitsarecorrupted,butmoreoftenthannotabursterroroccurs—severalconsecutivebitsarecorrupted.Bit
errorstypicallyoccurbecauseoutsideforces,suchaslightningstrikes,powersurges,andmicrowaveovens,interfere
withthetransmissionofdata.Thegoodnewsisthatsuchbiterrorsarefairlyrare,affectingonaverageonlyoneoutof
every10 to10 bitsonatypicalcopper-basedcableandoneoutofevery10 to10 bitsonatypicalopticalfiber.
Aswewillsee,therearetechniquesthatdetectthesebiterrorswithhighprobability.Oncedetected,itissometimes
possibletocorrectforsucherrors—ifweknowwhichbitorbitsarecorrupted,wecansimplyflipthem—whileinother
casesthedamageissobadthatitisnecessarytodiscardtheentirepacket.Insuchacase,thesendermaybe
expectedtoretransmitthepacket.
Thesecondclassoffailureisatthepacket,ratherthanthebit,level;thatis,acompletepacketislostbythenetwork.
Onereasonthiscanhappenisthatthepacketcontainsanuncorrectablebiterrorandthereforehastobediscarded.
Amorelikelyreason,however,isthatoneofthenodesthathastohandlethepacket—forexample,aswitchthatis
forwardingitfromonelinktoanother—issooverloadedthatithasnoplacetostorethepacketandthereforeisforced
6 7 12 14
1.2Requirements
19

todropit.Thisistheproblemofcongestionjustdiscussed.Lesscommonly,thesoftwarerunningononeofthenodes
thathandlesthepacketmakesamistake.Forexample,itmightincorrectlyforwardapacketoutonthewronglink,so
thatthepacketneverfindsitswaytotheultimatedestination.Aswewillsee,oneofthemaindifficultiesindealing
withlostpacketsisdistinguishingbetweenapacketthatisindeedlostandonethatismerelylateinarrivingatthe
destination.
Thethirdclassoffailureisatthenodeandlinklevel;thatis,aphysicallinkiscut,orthecomputeritisconnectedto
crashes.Thiscanbecausedbysoftwarethatcrashes,apowerfailure,orarecklessbackhoeoperator.Failuresdue
tomisconfigurationofanetworkdevicearealsocommon.Whileanyofthesefailurescaneventuallybecorrected,
theycanhaveadramaticeffectonthenetworkforanextendedperiodoftime.However,theyneednottotallydisable
thenetwork.Inapacket-switchednetwork,forexample,itissometimespossibletoroutearoundafailednodeorlink.
Oneofthedifficultiesindealingwiththisthirdclassoffailureisdistinguishingbetweenafailedcomputerandonethat
ismerelyslowor,inthecaseofalink,betweenonethathasbeencutandonethatisveryflakyandtherefore
introducingahighnumberofbiterrors.
Thekeyideatotakeawayfromthisdiscussionisthatdefiningusefulchannelsinvolvesbothunderstandingthe
applications'requirementsandrecognizingthelimitationsoftheunderlyingtechnology.Thechallengeistofillinthe
gapbetweenwhattheapplicationexpectsandwhattheunderlyingtechnologycanprovide.Thisissometimescalled
thesemanticgap.
Manageability
Afinalrequirement,whichseemstobeneglectedorlefttilllastalltoooften(aswedohere),isthatnetworksneedto
bemanaged.Managinganetworkincludesmakingchangesasthenetworkgrowstocarrymoretrafficorreachmore
users,andtroubleshootingthenetworkwhenthingsgowrongorperformanceisn'tasdesired.
Thisrequirementispartlyrelatedtotheissueofscalabilitydiscussedabove—astheInternethasscaleduptosupport
billionsofusersandatleasthundredsofmillionsofhosts,thechallengesofkeepingthewholethingrunningcorrectly
andcorrectlyconfiguringnewdevicesastheyareaddedhavebecomeincreasinglyproblematic.Configuringasingle
routerinanetworkisoftenataskforatrainedexpert;configuringthousandsofroutersandfiguringoutwhyanetwork
ofsuchasizeisnotbehavingasexpectedcanbecomeataskbeyondanysinglehuman.Furthermore,tomakethe
operationofanetworkscalableandcost-effective,networkoperatorstypicallyrequiremanymanagementtaskstobe
automatedoratleastperformedbyrelativelyunskilledpersonnel.
Animportantdevelopmentinnetworkingsincewewrotethefirsteditionofthisbookisthatnetworksinthehomeare
nowcommonplace.Thismeansthatnetworkmanagementisnolongertheprovinceofexpertsbutneedstobe
accomplishedbyconsumerswithlittletonospecialtraining.Thisissometimesstatedasarequirementthat
networkingdevicesshouldbe"plug-and-play"—agoalthathasprovenquiteelusive.Wewilldiscusssomewaysthat
thisrequirementhasbeenaddressedinpartlateron,butitisworthnotingfornowthatimprovingthemanageabilityof
networksremainsanimportantareaofcurrentresearch,ifnotthecentralchallengeinnetworkingtoday.
1.2Requirements
20
剩余434页未读,继续阅读
2011-10-31 上传
2019-01-12 上传
174 浏览量
2019-06-22 上传
2014-03-14 上传
2014-02-05 上传
2014-12-15 上传
brucezhao0
- 粉丝: 0
- 资源: 1
上传资源 快速赚钱
 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助

最新资源
- 探索数据转换实验平台在设备装置中的应用
- 使用git-log-to-tikz.py将Git日志转换为TIKZ图形
- 小栗子源码2.9.3版本发布
- 使用Tinder-Hack-Client实现Tinder API交互
- Android Studio新模板:个性化Material Design导航抽屉
- React API分页模块:数据获取与页面管理
- C语言实现顺序表的动态分配方法
- 光催化分解水产氢固溶体催化剂制备技术揭秘
- VS2013环境下tinyxml库的32位与64位编译指南
- 网易云歌词情感分析系统实现与架构
- React应用展示GitHub用户详细信息及项目分析
- LayUI2.1.6帮助文档API功能详解
- 全栈开发实现的chatgpt应用可打包小程序/H5/App
- C++实现顺序表的动态内存分配技术
- Java制作水果格斗游戏:策略与随机性的结合
- 基于若依框架的后台管理系统开发实例解析
安全验证
文档复制为VIP权益,开通VIP直接复制
 信息提交成功
信息提交成功