GUIDELINES ON ELECTRONIC MAIL SECURITY
2. Background and Standards
As of January 2007, the estimated number of Internet users worldwide exceeded one billion.
1
Most of
these users have electronic mail (email) accounts on one or more mail systems, which is a huge leap from
its inception in 1971, when Ray Tomlinson, a Department of Defense (DoD) researcher, sent the first
ARPANET email message to himself. The ARPANET, precursor to the Internet, was a United States
(U.S.) Advanced Research Project Agency (ARPA) project intended to develop a set of communications
protocols to transparently connect computing resources in various geographical locations. Messaging
applications were available on ARPANET systems; however, they could only be used for sending
messages to users with local system accounts. Tomlinson modified the existing messaging system so that
users could send messages to users on other ARPANET connected systems. After Tomlinson’s
modification was available to other researchers, email quickly became the most heavily used application
on the ARPANET.
As the ARPANET evolved into the Internet, email remained one of the most heavily used applications for
personal and business users. Since the ARPANET was initially a small and trusted community, there was
little need for security. The growth in the popularity of the Internet greatly increased the need for
security. Unfortunately, the needed security was lacking because early email standards and
implementations placed little emphasis on security. Maintaining compatibility with these standards
presents a great challenge in securing email today.
2.1 Background
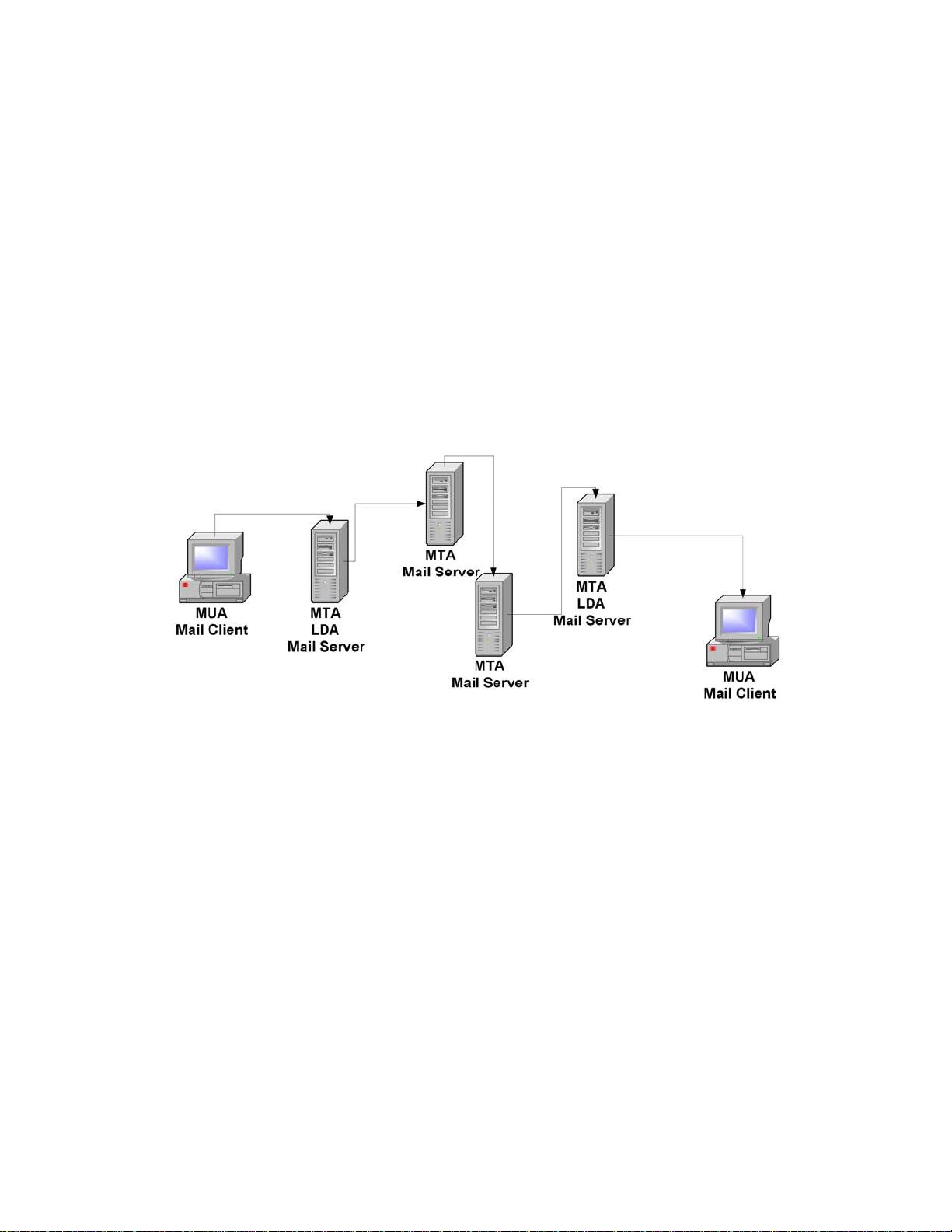
An understanding of how email messages are composed, delivered, and stored is helpful in understanding
email security. For most email users, once a message is composed and sent, it leaves the computer and
magically appears in the intended recipient’s inbox. This may seem simple but the handling and delivery
of an email message can be as complex as that involving physical mail, with processing and sorting
occurring at several intermediary locations before arriving at the final destination.
The process starts with message composition. The most basic mail clients typically ask the user to
provide the following: subject line, message content, and intended recipients. When these fields are
completed and the user sends the message, the message is transformed into a specific standard format
specified by Request for Comments (RFC) 2822, Internet Message Format. At the most basic level, the
two primary message sections are the header and the body. The header section contains the vital
information about the message including origination date, sender, recipient(s), delivery path, subject, and
format information. The body of the message contains the actual content of the message.
2
Once the message is translated into an RFC 2822 formatted message, it can be transmitted. Using a
network connection, the mail client, referred to as a mail user agent (MUA), connects to a mail transfer
agent (MTA) operating on the mail server. After initiating communication, the mail client provides the
sender’s identity to the server. Next, using the mail server commands, the client tells the server who the
intended recipients are. Although the message contains a list of intended recipients, the mail server does
not examine the message for this information. Only after the complete recipient list is sent to the server
does the client supply the message. From this point, message delivery is under control of the mail server.
1
World Internet Usage and Population Statistics, http://www.internetworldstats.com/stats.htm.
2
Refer to RFC 2822 for additional information on message headers. Appendix B contains a comprehensive list of email-
related RFCs that includes the URLs for many mail-related RFCs. It also indicates which RFCs are considered standards
and which are informational, standards in progress, or best current practices (BCP).
2-1