s1p
(id |id , R1)
s2p
(id |id , R2)
s3p
(id |id , R3)
(id |id , data)
p s
receiver (R2)
receiver (R1)
receiver (R3)
(b) Multicast
(id, R2)
sender (S)
(R2, data)
(id, R1)
(id, R3)
receiver (R2)
(R3, data)
receiver (R1)
(R1, data)
(id, data)
receiver (R3)
(c) Anycast
(R2, data)
sender (S)
(id, data)
sender (S)
receiver (R’)
(id, R)
(id, data)
sender (S)
receiver (R)
(R, data) (R’, data)(id, R’)
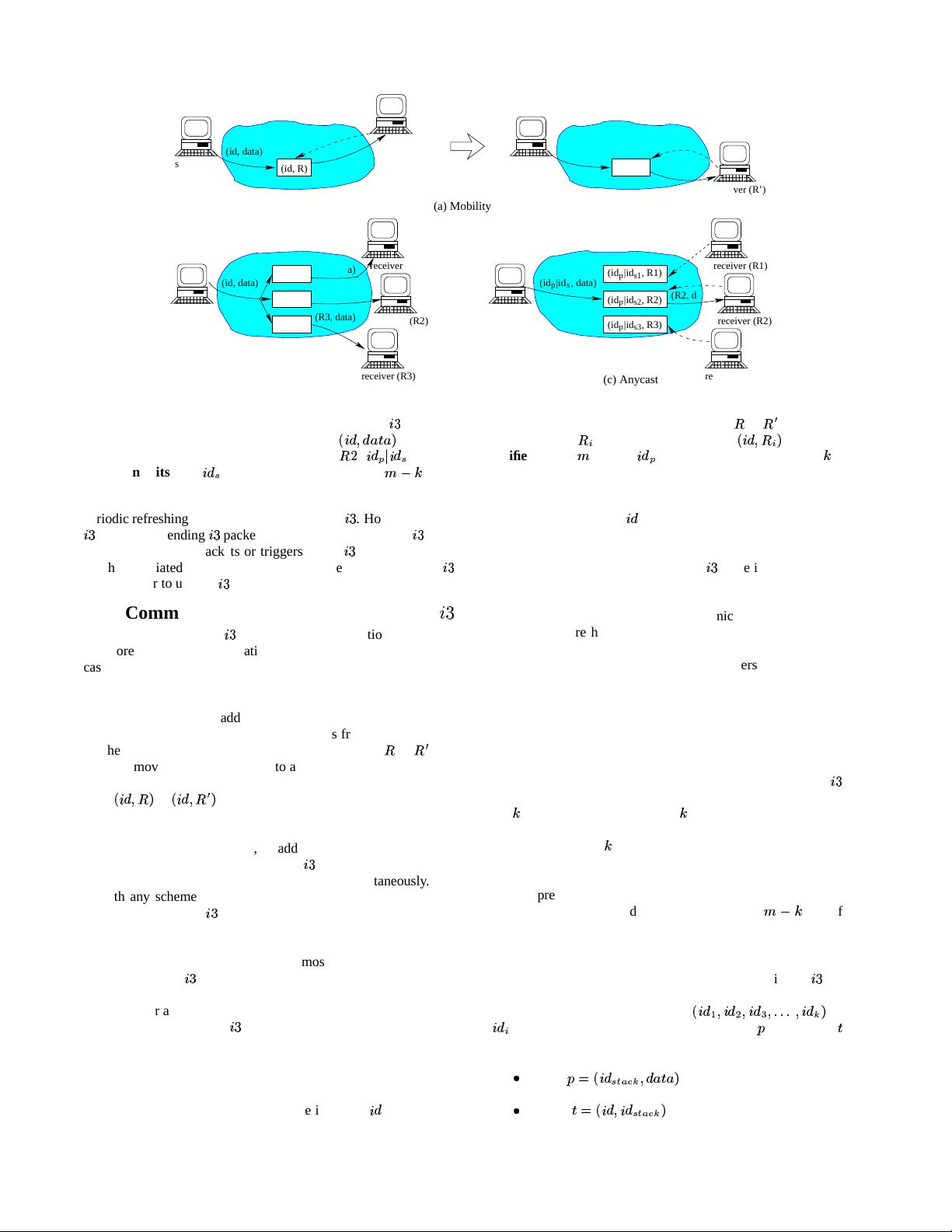
Figure 2: Communication abstractions provided by
. (a) Mobility: The change of the receiver’s address from
1
to
1
is transparent
to the sender. (b) Multicast: Every packet
2
!34398;:<8=6
is forwarded to each receiver
1
that inserts the trigger
2
@341
6
. (c) Anycast:
The packet matches the trigger of receiver
17L
.
@3
!
@3
#"
denotes an identifier of size
B
, where
@3
$
represents the prefix of the
D
most
significant bits, and
!3
"
represents the suffix of the
B
&%
D
least significant bits.
periodic refreshing to maintain their triggers in
. Hosts contact an
node when sending
packets or inserting triggers. This
node
then forwards these packets or triggers to the
node responsible
for the associated identifiers. Thus, hosts need only know one
node in order to use the
infrastructure.
2.4 Communication Primitives Provided by
>?
We now describe how
can be used by applications to achieve
the more general communication abstractions of mobility, multi-
cast, and anycast.
2.4.1 Mobility
The form of mobility addressed here is when a host (e.g., a lap-
top) is assigned a new address when it moves from one location to
another. A mobile host that changes its address from
1
to
1
'
as a
result of moving from one subnet to another can preserve the end-
to-end connectivity by simply updating each of its existing triggers
from
2
@34176
to
2
@341
6
, as shown in Figure 2(a). The sending host
needs not be aware of the mobile host’s current location or address.
Furthermore, since each packet is routed based on its identifier to
the server that stores its trigger, no additional operation needs to be
invoked when the sender moves. Thus,
can maintain end-to-end
connectivity even when both end-points move simultaneously.
With any scheme that supports mobility, efficiency is a major
concern [25]. With
, applications can use two techniques to
achieve efficiency. First, the address of the server storing the trigger
is cached at the sender, and thus subsequent packets are forwarded
directly to that server via IP. This way, most packets are forwarded
through only one
server in the overlay network. Second, to al-
leviate the triangle routing problem due to the trigger being stored
at a server far away, end-hosts can use off-line heuristics to choose
triggers that are stored at
servers close to themselves (see Sec-
tion 4.5 for details).
2.4.2 Multicast
Creating a multicast group is equivalent to having all members of
the group register triggers with the same identifier
!3
. As a result,
any packet that matches
@3
is forwarded to all members of the group
as shown in Figure 2(b). We discuss how to make this approach
scalable in Section 3.4.
Note that unlike IP multicast, with
there is no difference be-
tween unicast or multicast packets, in either sending or receiving.
Such an interface gives maximum flexibility to the application. An
application can switch on-the-fly from unicast to multicast by sim-
ply having more hosts maintain triggers with the same identifier.
For example, in a telephony application this would allow multiple
parties to seamlessly join a two-party conversation. In contrast,
with IP, an application has to at least change the IP destination ad-
dress in order to switch from unicast to multicast.
2.4.3 Anycast
Anycast ensures that a packet is delivered to exactly one receiver
in a group, if any. Anycast enables server selection, a basic building
block for many of today’s applications. To achieve this with
, all
hosts in an anycast group maintain triggers which are identical in
the
D
most significant bits. These
D
bits play the role of the anycast
group identifier. To send a packet to an anycast group, a sender uses
an identifier whose
D
-bit prefix matches the anycast group identi-
fier. The packet is then delivered to the member of the group whose
trigger identifier best matches the packet identifier according to the
longest prefix matching rule (see Figure 2(c)). Section 3.3 gives
two examples of how end-hosts can use the last
B
(%
D
bits of the
identifier to encode their preferences.
2.5 Stack of Identifiers
In this section, we describe a second generalization of
, which
replaces identifiers with identifier stacks. An identifier stack is a
list of identifiers that takes the form
2
!3
I
4
@3
*)
4
@3
#+
'4
-,.,-,
4
@3
*/
6
where
@3
#
is either an identifier or an address. Packets
0
and triggers
:
are
thus of the form:
1
Packet
0
J 2
@3
"
H
3254
/
453989:8=6
1
Trigger
:J 2
@34
@3
*"
<H
32-4
/
6









