Command to execute: ifconfig
Explanation: utility to configure network interfaces. It will be very useful to view the IP address assigned to a
machine.
Command to execute: traceroute
Explanation: this command allows you to trace the path of an IP packet to the host network. It is very useful for
performing troubleshooting activities such as, for example, verifying where in the path a certain IP packet stops
or is lost.
Command to execute: dig
Explanation: this is a utility needed to query DNS. There would be plenty of other things to say about this
command and its functioning is quite complex. You will understand its mechanisms better in the next few
chapters when I will explain what a DNS is and how we can organize an attack against it.
Command to execute: telnet
Explanation: this command allows us to make connections to remote hosts via the TELNET protocol. I want to
clarify that this protocol allows a clear visualization of data without any encryption mechanisms. For this reason,
it is not a very secure protocol.
Command to execute: telnet
Explanation: this command allows us to make connections to remote hosts via the TELNET protocol. I want to
clarify that this protocol allows a clear visualization of data without any encryption mechanisms. For this reason,
it is not a very secure protocol.
Command to execute: nslookup
Explanation: this is another utility to interrogate DNS and to perform inverse resolution queries. In our
exercises, we will often use this command.
Command to execute: netstat
Explanation: this is a command of the utmost importance. It allows you to view the network connections
opened at a certain time. Useful in troubleshooting, it allows us to verify anomalies due to network connections
that were not established or lost. Here again, take some time to improve your knowledge of this tool.
Command to execute: ifup, ifdown
Explanation: this command allows you to enable or disable network cards. It can be very useful in certain
situations, perhaps when a reboot of network services is required.
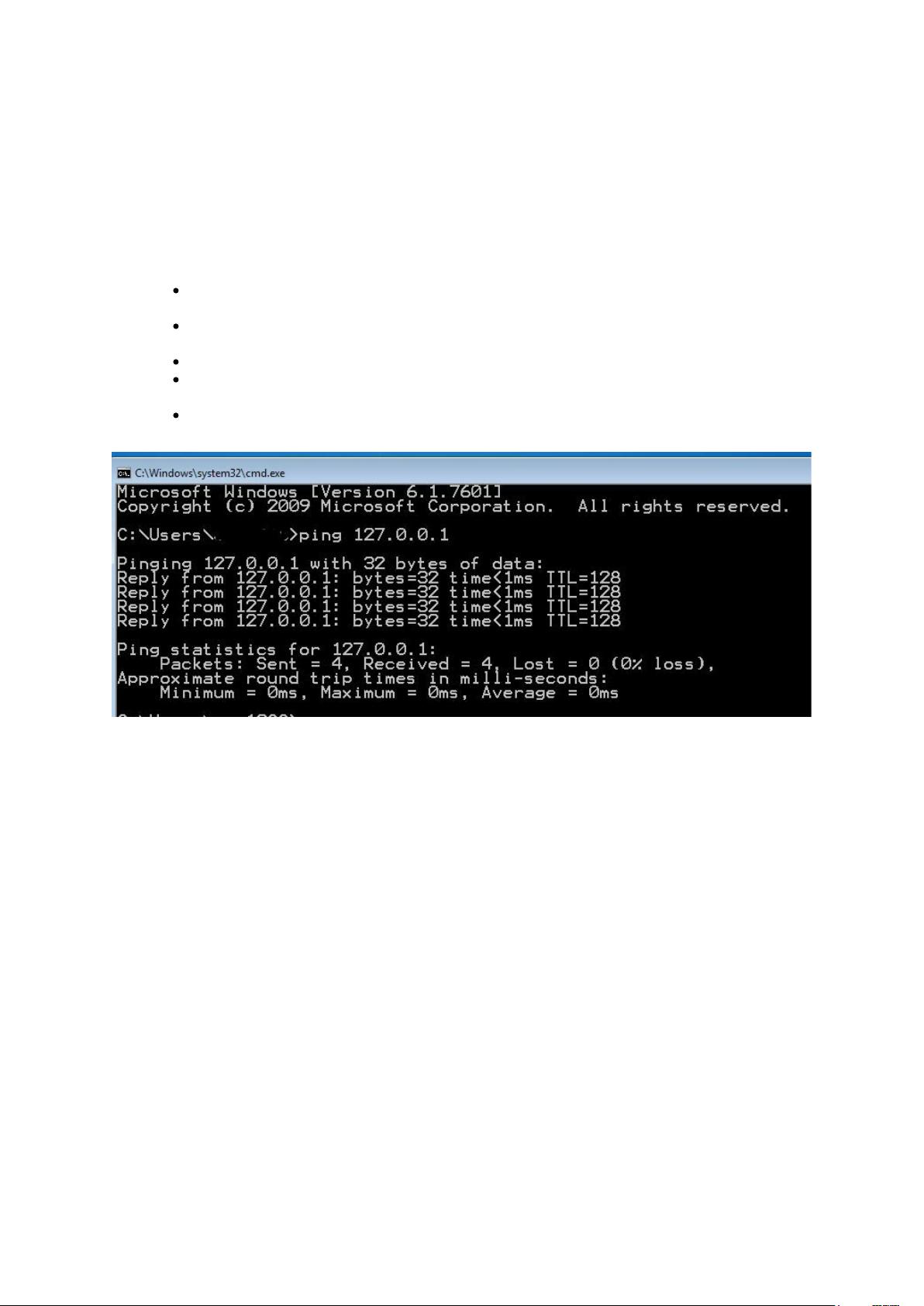
Command to execute: ping
Explanation: the PING command is used to check whether a certain host is active or not by sending special
ICMP type packets to it and waiting for a response. Let me remind you that we have already used it in our
penetration testing lab to verify the connectivity between the various virtual machines.
Command to execute: route
Explanation: this command is used to display the routing table of a certain host, namely the paths that the
network packets must perform on the network or on particular subnets.
Command to execute: arp -a
Explanation: the ARP -A command provides us with a table of the links between a MAC address and an IP
address. For example, it can be used when we want to exclude problems concerning the lower levels of the
ISO/OSI model (data level).
Here are all the commands related to networking. Of course, this list does not include them all, there would be
much more to say. However, you will do great later if you begin to become familiar with these commands.
COMMANDS RELATED TO SYSTEM MANAGEMENT
Let's now move on to the last part of the Linux commands, which are related to the ordinary management of
your Linux machine.
Command to execute: uptime
Explanation: this command shows you for how long a certain system has been active.
Command to execute: users
Explanation: this command shows the user names of users connected to a system.
Command to execute: who / whoami