首页
exploiting cloze questions for few shot text classification and natural language inference
exploiting cloze questions for few shot text classification and natural language inference
时间: 2023-04-30 07:05:28
浏览: 207
题目翻译:利用填空题进行少样本文本分类和自然语言推理。 这篇论文使用填空题来辅助进行少样本文本分类和自然语言推理任务。作者利用已有的模型预测填空题的答案,并将预测结果作为样本的特征。结果表明,这种方法可以提高任务的准确率和泛化能力。
阅读全文
相关推荐
Triplex transfer learning: Exploiting both shared and distinct concepts for text classification
在文本分类领域,转移学习是一种重要的机器学习方法,它主要关注当源域中的训练数据和目标域中的测试数据虽然在原始特征上具有相似的分布,但仍然存在差异时的学习情景。在转移学习的研究中,一些近期的文献指出,...
Exploiting the categorical reliability difference for binary classification
### 利用类别可靠性差异进行二元分类 #### 摘要 在二元模式分类问题中,两类样本所获得的统计信息的可靠性通常存在差异。当这些统计信息被用于构建分类器时,这种可靠性差异可能会影响分类器的泛化性能。...
Modeling and exploiting tag relevance for Web service mining
Modeling and exploiting tag relevance for Web service mining
Exploiting Reflection Change for Automatic Reflection Removal
《利用反射变化自动消除图像反射》是一篇关于图像处理技术的深度研究,主要探讨了如何通过分析和利用图像中的反射变化来实现自动化地去除图像中的反射现象。在图像处理领域,尤其是在摄影、数字媒体和视觉识别中,...
SegStereo: Exploiting Semantic Information for Disparity Estimation
Disparity estimation for binocular stereo images finds a wide range of applications. Traditional algorithms may fail on featureless regions, which could be handled by high-level clues such as semantic...
Exploiting multiple sources for open-domain hypernym discovery
本文主要讨论了在开放域中利用多种来源发现上位词(hypernym discovery)的技术与方法。上位词,也称为超类词或泛化词,在自然语言处理(NLP)中指的是具有概括或分类关系的一对名词,其中一个名词可以是另一个名词...
Exploiting Optimal Threshold for Decision Fusion in Wireless Sensor Networks
Decision fusion has been adopted in a number of sensor systems to deal with sensing uncertainty and enable the sensors to collaborate with each other. It can distribute computation workload and ...
Exploiting Channel Diversity for Rate Adaptation in Backscatter Communication Networks
### 利用信道多样性进行背散射通信网络中的速率自适应 #### 摘要与背景 近年来,背散射通信网络因其小巧的尺寸和低功耗特性而备受关注。这种类型的网络非常适合用于构建感知和计算平台,例如射频识别(RFID)系统...
Exploiting social circlebroadness for influential spreaders identification in social networks
这篇文章的标题和描述涉及到了社交网络中信息传播的影响力用户识别问题,并提出了利用社交圈广度(social circle broadness)作为新指标来衡量用户的影响力。文章的主要贡献和知识点如下: 1. 影响力用户识别的重要...
Exploiting Process Variation for Retention Induced Refresh Minimization on Flash Memory
Solid state drives (SSDs) are becoming the default storage medium with the cost dropping of NAND flash memory. However, the cost dropping driven by the density improvement and technology ...
HDNET- Exploiting HD Maps for 3D Object Detection.pdf
在这篇文章中,作者们提出了一种名为HDNET的单阶段检测器,它能够从高清地图(HD Maps)中提取几何和语义特征来增强现代3D物体检测器的性能和鲁棒性。文章主要探讨了无人驾驶领域中,通过整合地图信息来提高3D物体检测...
[学位论文——博士]Exploiting Wireless Systems for Covert
该博士论文的主题是无线隐蔽通信系统,探讨了隐藏通信信号的技术手段,其研究目的在于通过无线网络的物理层实现隐蔽通信。在网络安全领域,隐蔽通信指的是通过各种技术手段使得通信内容对未授权的第三方不可见,或者...
Exploiting mobility patterns for inter-technology handover in mobile environments
This makes it possible for Internet applications to be supported by heterogeneous wireless networks while the terminal is on the move. As the user is constantly moving, it is highly desirable that ...
HDNET- Exploiting HD Maps for 3D Object Detection.zip
《HDNET:利用高清地图进行三维物体检测》 在自动驾驶和智能交通系统中,精确的三维物体检测是一项至关重要的技术。这项技术能够帮助车辆、无人机等设备识别周围环境中的行人、车辆、交通标志等物体,确保安全行驶...
Exploiting Event-Based Communication for Real-Time Distributed and Parallel Video Content Analysis
### 关键知识点解析 #### 一、研究背景与动机 - **数字视频技术的发展**:随着数字视频技术的快速发展及成本下降,生产数字视频的设备变得越来越便宜且普及。 - **无线技术的进步**:无线技术的进步使得具备网络...
CoCo+: Exploiting Correlated Core for Energy Efficient Dissemination in Wireless Sensor Networks
在无线传感器网络中,能量效率是一个核心问题,因为在许多应用中,传感器节点的能量供应是有限的,且不易更换。传输和接收数据是最耗能的操作之一,因此,设计有效的数据传播算法对于延长无线传感器网络的寿命至关...
A multiclassifier and decision fusion system for hyperspectral image classification
In this paper, a windowed three-dimensional discrete wavelet transform (3DDWT) is employed to extract spectral-spatial features for hyperspectral image classification; these features quantify local ...
Exploiting Social Influence for Context-Aware Event Recommendation in Event-based Social Networks
事件推荐系统和社交网络在现代网络社会中扮演着重要的角色,它们通过连接线上线下用户的互动活动,对用户日常生活的各个方面产生影响。在众多研究领域中,基于事件的社交网络(Event-based Social Networks, EBSNs)...
内墙装修涂料行业发展趋势:预计2030年年复合增长率(CAGR)为5.6%(2024-2030)
内墙装修涂料市场:把握5.6%年复合增长率 在追求舒适与美观并重的现代家居生活中,内墙装修涂料扮演着至关重要的角色。它不仅关乎居室的视觉效果,更与居住者的健康息息相关。令人振奋的是,这一数据背后,隐藏着怎样的市场机遇与挑战?让我们一同探索内墙装修涂料的未来之路。 市场概况: 根据QYR(恒州博智)的统计及预测,2023年全球内墙装修涂料市场销售额达到了149亿元,预计2030年将达到213亿元,年复合增长率(CAGR)为5.6%(2024-2030)。这一增长不仅源于消费者对居住环境品质要求的提升,更得益于技术创新和环保理念的深入人心。 技术创新与趋势: 在内墙装修涂料领域,技术创新是推动市场发展的重要力量。随着环保法规的日益严格和消费者环保意识的增强,低VOC(挥发性有机化合物)、无毒、抗菌等环保型涂料逐渐成为市场主流。同时,智能化、个性化等趋势也日益明显,如通过APP控制涂料颜色、质感等,满足消费者多元化的装修需求。咨询服务在此过程中的价值不言而喻,它能帮助企业紧跟市场趋势,把握技术创新方向,从而在竞争中脱颖而出。 应用领域与细分市场: 内墙装修涂料广泛应用于住宅、酒店、学校、医院
CSDN会员
开通CSDN年卡参与万元壕礼抽奖
海量
VIP免费资源
千本
正版电子书
商城
会员专享价
千门
课程&专栏
全年可省5,000元
立即开通
全年可省5,000元
立即开通
大家在看
公安大数据零信任体系设计要求.pdf
公安大数据零信任体系设计要求,本规范性技术文件规定了零信任体系的整体设计原则、设计目标、总体架构、整体能力要求和安全流程。用以指导公安大数据智能化访问控制体系的规划、设计、建设、实施、应用、运营等工作。 本规范性技术文件适用于参与公安机关大数据智能化访问控制体系建设工作的各级公安机关、相关单位、以及各类技术厂商等单位及其人员。
AUTOSAR-MCAL -CanDriver-UserMAnnual
EB Tresos,CAN驱动用户手册,有助于进行CAN模块配置及配置项研究
MTK_Camera_HAL3架构.doc
适用于MTK HAL3架构,介绍AppStreamMgr , pipelineModel, P1Node,P2StreamingNode等模块
不平衡学习的自适应合成采样方法ADASYN附Matlab代码.zip
1.版本:matlab2014/2019a,内含运行结果,不会运行可私信 2.领域:智能优化算法、神经网络预测、信号处理、元胞自动机、图像处理、路径规划、无人机等多种领域的Matlab仿真,更多内容可点击博主头像 3.内容:标题所示,对于介绍可点击主页搜索博客 4.适合人群:本科,硕士等教研学习使用 5.博客介绍:热爱科研的Matlab仿真开发者,修心和技术同步精进,matlab项目合作可si信
山东大学最优化方法期末整合(多套)
往年期末题
最新推荐
DES对称分组密码系统的Java实现
//Exploiting the results print("Byte array of cipher:"); for(int i=0;i;i++) System.out.print(ct[i]+" "); print(""); for(int i=0;i;i++) ct[i]=(byte)(ct[i]&0xFF); String ciphertxt=new String(ct)...
内墙装修涂料行业发展趋势:预计2030年年复合增长率(CAGR)为5.6%(2024-2030)
内墙装修涂料市场:把握5.6%年复合增长率 在追求舒适与美观并重的现代家居生活中,内墙装修涂料扮演着至关重要的角色。它不仅关乎居室的视觉效果,更与居住者的健康息息相关。令人振奋的是,这一数据背后,隐藏着怎样的市场机遇与挑战?让我们一同探索内墙装修涂料的未来之路。 市场概况: 根据QYR(恒州博智)的统计及预测,2023年全球内墙装修涂料市场销售额达到了149亿元,预计2030年将达到213亿元,年复合增长率(CAGR)为5.6%(2024-2030)。这一增长不仅源于消费者对居住环境品质要求的提升,更得益于技术创新和环保理念的深入人心。 技术创新与趋势: 在内墙装修涂料领域,技术创新是推动市场发展的重要力量。随着环保法规的日益严格和消费者环保意识的增强,低VOC(挥发性有机化合物)、无毒、抗菌等环保型涂料逐渐成为市场主流。同时,智能化、个性化等趋势也日益明显,如通过APP控制涂料颜色、质感等,满足消费者多元化的装修需求。咨询服务在此过程中的价值不言而喻,它能帮助企业紧跟市场趋势,把握技术创新方向,从而在竞争中脱颖而出。 应用领域与细分市场: 内墙装修涂料广泛应用于住宅、酒店、学校、医院
HTML挑战:30天技术学习之旅
资源摘要信息: "desafio-30dias" 标题 "desafio-30dias" 暗示这可能是一个与挑战或训练相关的项目,这在编程和学习新技能的上下文中相当常见。标题中的数字“30”很可能表明这个挑战涉及为期30天的时间框架。此外,由于标题是西班牙语,我们可以推测这个项目可能起源于或至少是针对西班牙语使用者的社区。标题本身没有透露技术上的具体内容,但挑战通常涉及一系列任务,旨在提升个人的某项技能或知识水平。 描述 "desafio-30dias" 并没有提供进一步的信息,它重复了标题的内容。因此,我们不能从中获得关于项目具体细节的额外信息。描述通常用于详细说明项目的性质、目标和期望成果,但由于这里没有具体描述,我们只能依靠标题和相关标签进行推测。 标签 "HTML" 表明这个挑战很可能与HTML(超文本标记语言)有关。HTML是构成网页和网页应用基础的标记语言,用于创建和定义内容的结构、格式和语义。由于标签指定了HTML,我们可以合理假设这个30天挑战的目的是学习或提升HTML技能。它可能包含创建网页、实现网页设计、理解HTML5的新特性等方面的任务。 压缩包子文件的文件名称列表 "desafio-30dias-master" 指向了一个可能包含挑战相关材料的压缩文件。文件名中的“master”表明这可能是一个主文件或包含最终版本材料的文件夹。通常,在版本控制系统如Git中,“master”分支代表项目的主分支,用于存放项目的稳定版本。考虑到这个文件名称的格式,它可能是一个包含所有相关文件和资源的ZIP或RAR压缩文件。 结合这些信息,我们可以推测,这个30天挑战可能涉及了一系列的编程任务和练习,旨在通过实践项目来提高对HTML的理解和应用能力。这些任务可能包括设计和开发静态和动态网页,学习如何使用HTML5增强网页的功能和用户体验,以及如何将HTML与CSS(层叠样式表)和JavaScript等其他技术结合,制作出丰富的交互式网站。 综上所述,这个项目可能是一个为期30天的HTML学习计划,设计给希望提升前端开发能力的开发者,尤其是那些对HTML基础和最新标准感兴趣的人。挑战可能包含了理论学习和实践练习,鼓励参与者通过构建实际项目来学习和巩固知识点。通过这样的学习过程,参与者可以提高在现代网页开发环境中的竞争力,为创建更加复杂和引人入胜的网页打下坚实的基础。
【CodeBlocks精通指南】:一步到位安装wxWidgets库(新手必备)
 # 摘要 本文旨在为使用CodeBlocks和wxWidgets库的开发者提供详细的安装、配置、实践操作指南和性能优化建议。文章首先介绍了CodeBlocks和wxWidgets库的基本概念和安装流程,然后深入探讨了CodeBlocks的高级功能定制和wxWidgets的架构特性。随后,通过实践操作章节,指导读者如何创建和运行一个wxWidgets项目,包括界面设计、事件
andorid studio 配置ERROR: Cause: unable to find valid certification path to requested target
### 解决 Android Studio SSL 证书验证问题 当遇到 `unable to find valid certification path` 错误时,这通常意味着 Java 运行环境无法识别服务器提供的 SSL 证书。解决方案涉及更新本地的信任库或调整项目中的网络请求设置。 #### 方法一:安装自定义 CA 证书到 JDK 中 对于企业内部使用的私有 CA 颁发的证书,可以将其导入至 JRE 的信任库中: 1. 获取 `.crt` 或者 `.cer` 文件形式的企业根证书; 2. 使用命令行工具 keytool 将其加入 cacerts 文件内: ```
VC++实现文件顺序读写操作的技巧与实践
资源摘要信息:"vc++文件的顺序读写操作" 在计算机编程中,文件的顺序读写操作是最基础的操作之一,尤其在使用C++语言进行开发时,了解和掌握文件的顺序读写操作是十分重要的。在Microsoft的Visual C++(简称VC++)开发环境中,可以通过标准库中的文件操作函数来实现顺序读写功能。 ### 文件顺序读写基础 顺序读写指的是从文件的开始处逐个读取或写入数据,直到文件结束。这与随机读写不同,后者可以任意位置读取或写入数据。顺序读写操作通常用于处理日志文件、文本文件等不需要频繁随机访问的文件。 ### VC++中的文件流类 在VC++中,顺序读写操作主要使用的是C++标准库中的fstream类,包括ifstream(用于从文件中读取数据)和ofstream(用于向文件写入数据)两个类。这两个类都是从fstream类继承而来,提供了基本的文件操作功能。 ### 实现文件顺序读写操作的步骤 1. **包含必要的头文件**:要进行文件操作,首先需要包含fstream头文件。 ```cpp #include <fstream> ``` 2. **创建文件流对象**:创建ifstream或ofstream对象,用于打开文件。 ```cpp ifstream inFile("example.txt"); // 用于读操作 ofstream outFile("example.txt"); // 用于写操作 ``` 3. **打开文件**:使用文件流对象的成员函数open()来打开文件。如果不需要在创建对象时指定文件路径,也可以在对象创建后调用open()。 ```cpp inFile.open("example.txt", std::ios::in); // 以读模式打开 outFile.open("example.txt", std::ios::out); // 以写模式打开 ``` 4. **读写数据**:使用文件流对象的成员函数进行数据的读取或写入。对于读操作,可以使用 >> 运算符、get()、read()等方法;对于写操作,可以使用 << 运算符、write()等方法。 ```cpp // 读取操作示例 char c; while (inFile >> c) { // 处理读取的数据c } // 写入操作示例 const char *text = "Hello, World!"; outFile << text; ``` 5. **关闭文件**:操作完成后,应关闭文件,释放资源。 ```cpp inFile.close(); outFile.close(); ``` ### 文件顺序读写的注意事项 - 在进行文件读写之前,需要确保文件确实存在,且程序有足够的权限对文件进行读写操作。 - 使用文件流进行读写时,应注意文件流的错误状态。例如,在读取完文件后,应检查文件流是否到达文件末尾(failbit)。 - 在写入文件时,如果目标文件不存在,某些open()操作会自动创建文件。如果文件已存在,open()操作则会清空原文件内容,除非使用了追加模式(std::ios::app)。 - 对于大文件的读写,应考虑内存使用情况,避免一次性读取过多数据导致内存溢出。 - 在程序结束前,应该关闭所有打开的文件流。虽然文件流对象的析构函数会自动关闭文件,但显式调用close()是一个好习惯。 ### 常用的文件操作函数 - `open()`:打开文件。 - `close()`:关闭文件。 - `read()`:从文件读取数据到缓冲区。 - `write()`:向文件写入数据。 - `tellg()` 和 `tellp()`:分别返回当前读取位置和写入位置。 - `seekg()` 和 `seekp()`:设置文件流的位置。 ### 总结 在VC++中实现顺序读写操作,是进行文件处理和数据持久化的基础。通过使用C++的标准库中的fstream类,我们可以方便地进行文件读写操作。掌握文件顺序读写不仅可以帮助我们在实际开发中处理数据文件,还可以加深我们对C++语言和文件I/O操作的理解。需要注意的是,在进行文件操作时,合理管理和异常处理是非常重要的,这有助于确保程序的健壮性和数据的安全。
【大数据时代必备:Hadoop框架深度解析】:掌握核心组件,开启数据科学之旅
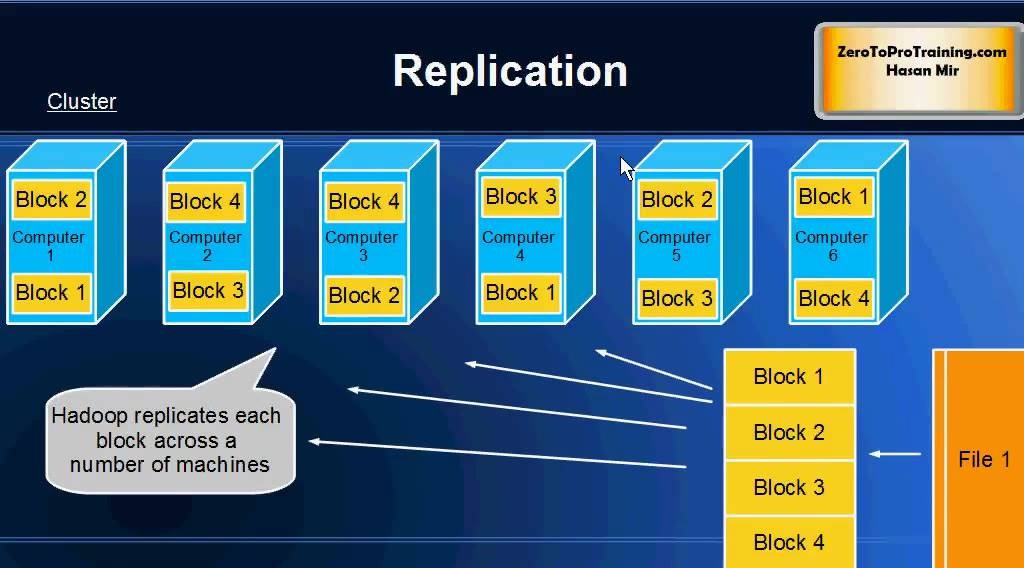 # 摘要 Hadoop作为一个开源的分布式存储和计算框架,在大数据处理领域发挥着举足轻重的作用。本文首先对Hadoop进行了概述,并介绍了其生态系统中的核心组件。深入分
opencv的demo程序
### OpenCV 示例程序 #### 图像读取与显示 下面展示如何使用 Python 接口来加载并显示一张图片: ```python import cv2 # 加载图像 img = cv2.imread('path_to_image.jpg') # 创建窗口用于显示图像 cv2.namedWindow('image', cv2.WINDOW_AUTOSIZE) # 显示图像 cv2.imshow('image', img) # 等待按键事件 cv2.waitKey(0) # 销毁所有创建的窗口 cv2.destroyAllWindows() ``` 这段代码展示了最基本的图
NeuronTransportIGA: 使用IGA进行神经元材料传输模拟
资源摘要信息:"matlab提取文件要素代码-NeuronTransportIGA:该软件包使用等几何分析(IGA)在神经元的复杂几何形状中执行材料传输模拟" 标题中提到的"NeuronTransportIGA"是一个使用等几何分析(Isogeometric Analysis, IGA)技术的软件包,该技术在处理神经元这样复杂的几何形状时进行材料传输模拟。等几何分析是一种新兴的数值分析方法,它利用与计算机辅助设计(CAD)相同的数学模型,从而提高了在仿真中处理复杂几何结构的精确性和效率。 描述中详细介绍了NeuronTransportIGA软件包的使用流程,其中包括网格生成、控制网格文件的创建和仿真工作的执行。具体步骤包括: 1. 网格生成(Matlab):首先,需要使用Matlab代码对神经元骨架进行平滑处理,并生成用于IGA仿真的六面体控制网格。这里所指的“神经元骨架信息”通常以.swc格式存储,它是一种描述神经元三维形态的文件格式。网格生成依赖于一系列参数,这些参数定义在mesh_parameter.txt文件中。 2. 控制网格文件的创建:根据用户设定的参数,生成的控制网格文件是.vtk格式的,通常用于可视化和分析。其中,controlmesh.vtk就是最终生成的六面体控制网格文件。 在使用过程中,用户需要下载相关代码文件,并放置在meshgeneration目录中。接着,使用TreeSmooth.m代码来平滑输入的神经元骨架信息,并生成一个-smooth.swc文件。TreeSmooth.m脚本允许用户在其中设置平滑参数,影响神经元骨架的平滑程度。 接着,使用Hexmesh_main.m代码来基于平滑后的神经元骨架生成六面体网格。Hexmesh_main.m脚本同样需要用户设置网格参数,以及输入/输出路径,以完成网格的生成和分叉精修。 此外,描述中也提到了需要注意的“笔记”,虽然具体笔记内容未给出,但通常这类笔记会涉及到软件包使用中可能遇到的常见问题、优化提示或特殊设置等。 从标签信息“系统开源”可以得知,NeuronTransportIGA是一个开源软件包。开源意味着用户可以自由使用、修改和分发该软件,这对于学术研究和科学计算是非常有益的,因为它促进了研究者之间的协作和知识共享。 最后,压缩包子文件的文件名称列表为"NeuronTransportIGA-master",这表明了这是一个版本控制的源代码包,可能使用了Git版本控制系统,其中"master"通常是指默认的、稳定的代码分支。 通过上述信息,我们可以了解到NeuronTransportIGA软件包不仅仅是一个工具,它还代表了一个研究领域——即使用数值分析方法对神经元中的物质传输进行模拟。该软件包的开发和维护为神经科学、生物物理学和数值工程等多个学科的研究人员提供了宝贵的资源和便利。
【Linux多系统管理大揭秘】:专家级技巧助你轻松驾驭
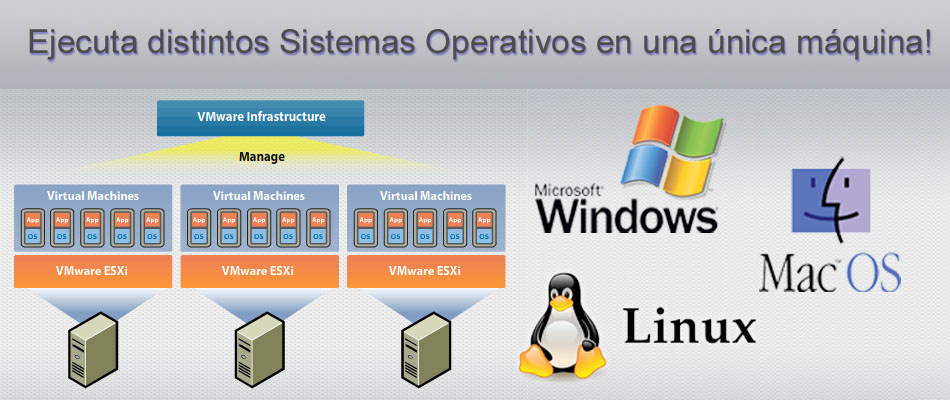 # 摘要 本文全面介绍了Linux多系统管理的关键技术和最佳实践。首先概述了多系统管理的基本概念,随后详细探讨了多系统的安装与启动流程,包括系统安装前的准备工作、各主流Linux发行版的安装方法以及启动管理器GRUB2的配置。接下来,文章深入分析了Linux多系统间文件共享与数据迁移的策略,特别是NTFS与Linux文件系统的互操作性和网络文件系统(NFS)的应用。此外,本