理论神经科学:研究生版
需积分: 20 41 浏览量
更新于2024-07-09
收藏 7.94MB PDF 举报
"Theoretical Neuroscience for Graduate-Edition4 .pdf"
本书是针对研究生级别的理论神经科学教材,由Peter Dayan和L.F. Abbott撰写。它深入探讨了神经元响应的分析和建模方法,旨在帮助读者理解大脑如何处理信息。
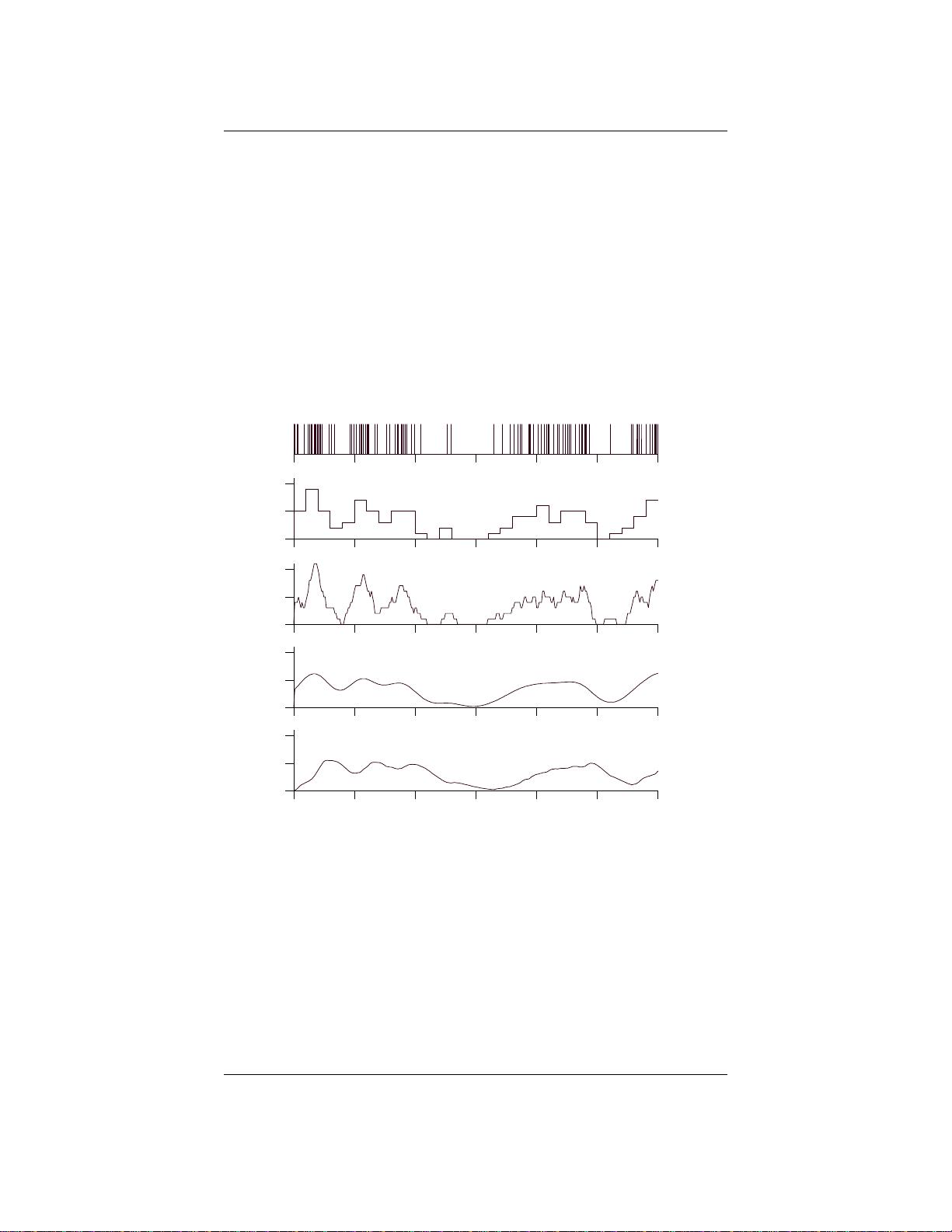
在第一章“神经编码I:放电率与尖峰统计”中,作者首先介绍了神经元的基本属性,如它们是如何记录和传递信息的。神经元响应通常通过记录其放电活动(尖峰)来研究,从刺激到响应的转换过程被详细阐述。放电率是衡量神经元活动强度的一个关键指标,用于描述神经元对特定刺激的反应程度。调谐曲线则展示了神经元对不同刺激的敏感度。
尖峰计数变异性是另一个重要的概念,它讨论了神经元放电模式的不稳定性。接下来,作者探讨了什么因素能触发神经元放电,以及如何通过描述刺激来理解这一过程。其中,尖峰触发平均值(Spike-Triggered Average)被用来揭示神经元对特定刺激片段的反应模式。白噪声刺激被广泛使用,因为它可以提供丰富的刺激信息。此外,还讨论了多个尖峰触发平均值和尖峰触发相关性,这些对于理解神经元间的交互作用至关重要。
在尖峰序列统计部分,作者介绍了齐次泊松过程和非齐次泊松过程,以及它们在模拟神经放电中的应用。这些统计模型与实际神经数据进行比较,以评估其适用性。书中还探讨了神经编码的不同类型,如独立尖峰、独立神经元编码和相关编码,以及时间编码的概念,这些编码方式都反映了神经信息传输的复杂性。
第二章“神经编码II:反向相关和感受野”进一步深入,介绍了一种估计放电率的方法——反向相关法,这是理解神经元感受野(Receptive Fields)的重要工具。反向相关法可以帮助研究人员识别神经元对输入信号的响应特征,从而揭示神经元如何编码视觉、听觉等感官信息。
这本书涵盖了神经科学中从基本的神经元特性到高级的编码策略等多个层次的内容,结合数学模型和统计方法,为研究生提供了全面理解神经信息处理的基础。书中还包含了丰富的附录和参考文献,以便于读者进一步探索相关主题。
2017-11-19 上传
2018-09-27 上传
2020-04-06 上传
2023-05-13 上传
2023-06-02 上传
2023-05-19 上传
2023-06-01 上传
2023-06-11 上传
2023-06-13 上传
scl712
- 粉丝: 0
- 资源: 5
最新资源
- C语言数组操作:高度检查器编程实践
- 基于Swift开发的嘉定单车LBS iOS应用项目解析
- 钗头凤声乐表演的二度创作分析报告
- 分布式数据库特训营全套教程资料
- JavaScript开发者Robert Bindar的博客平台
- MATLAB投影寻踪代码教程及文件解压缩指南
- HTML5拖放实现的RPSLS游戏教程
- HT://Dig引擎接口,Ampoliros开源模块应用
- 全面探测服务器性能与PHP环境的iprober PHP探针v0.024
- 新版提醒应用v2:基于MongoDB的数据存储
- 《我的世界》东方大陆1.12.2材质包深度体验
- Hypercore Promisifier: JavaScript中的回调转换为Promise包装器
- 探索开源项目Artifice:Slyme脚本与技巧游戏
- Matlab机器人学习代码解析与笔记分享
- 查尔默斯大学计算物理作业HP2解析
- GitHub问题管理新工具:GIRA-crx插件介绍