© 2001 John Viega and Gary McGraw
6
“local”. In a remote attack, a malicious attacker can break onto a machine that is
connected to the same network, usually through some flaw in software. If the software is
available through a firewall, then the firewall will be useless. In a local attack, a
malicious user can gain additional privileges on a machine, usually administrative
privileges. Most security experts agree that once an attacker has a foothold on your
machine, it is incredibly difficult to keep them from getting administrative access;
operating systems and the privileged applications that are generally found on them
constitute such a large and complex body of code that the presence of some security hole
unknown to the masses (or at least the system administrator) is always likely.
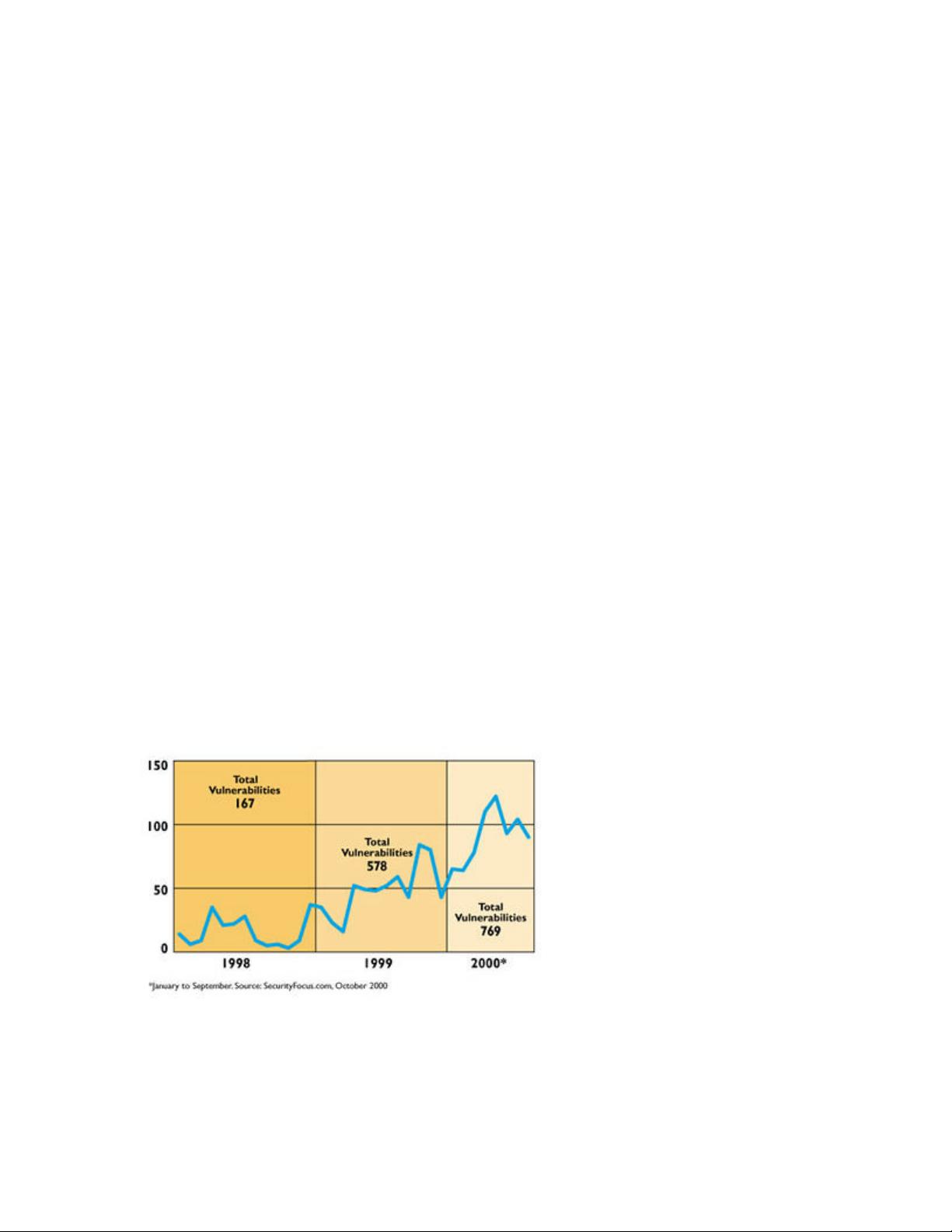
Nonetheless, both kinds of problems are important, and it is important for companies
wishing to be secure to keep up with security vulnerabilities in software. There are
several popular sources for vulnerability information:
Bugtraq. The Bugtraq mailing list, administered by securityfocus.com, is an e-mail
discussion list devoted to security issues. Many security vulnerabilities are proposed,
scripted, and patched on Bugtraq (which generates a large amount of traffic). The signal
to noise ratio on Bugtraq is low, so reader discretion is advised. Nevertheless, this list is
often the source of breaking security news and interesting technical discussion. Plenty of
computer security reporters use Bugtraq as their primary source of information.
Bugtraq is famous for pioneering the principle of “full disclosure”, which is a debated
notion that making full information about security vulnerabilities public will encourage
vendors to fix such problems more quickly. This philosophy was driven by numerous
documented cases of vendors downplaying security problems, refusing to fix them when
they believed that few of their customers would find out about any problems.
If the signal to noise ratio on Bugtraq is too low for your tastes, the securityfocus.com
web site keeps good information on recent vulnerabilities.
CERT Advisories. The CERT Coordination Center (CERT/CC, www.cert.org) is located
at the Software Engineering Institute, a federally funded research and development center
operated by Carnegie Mellon University. CERT/CC studies Internet security
vulnerabilities, provides incident response services to sites that have been the victims of
attack, and publishes a variety of security alerts.
Many people in the security community complain that CERT/CC announces problems
much too late to be effective. For example, a problem in the TCP protocol was the subject
of a CERT advisory released a decade after the flaw was first made public. Delays
experienced in the past can largely be attributed to the (since changed) policy of not
publicizing an attack until patches were available. However, problems like the
aforementioned TCP vulnerability are more likely attributed to the small size of CERT.
CERT tends only to release advisories for significant problems. In this case, they reacted
once the problem was being commonly exploited in the wild. The advantage of
CERT/CC as a knowledge source is that they highlight attacks that are in actual use, and